
You answer your phone and hear a calm, confident voice:
‘Hello, this is the fraud department from your bank. We detected an unusual transaction on your account. Before we proceed, can you confirm your customer ID and the OTP you will receive shortly?’
The caller sounds professional. The number looks official. The situation feels urgent. Most people would comply – and that’s exactly why vishing, or voice phishing, has become one of the most successful forms of social engineering today.
Unlike text or email scams, vishing leverages the human voice to manipulate people in real time. Instead of hacking systems, attackers manipulate emotions like trust, urgency, and compliance to convince individuals to disclose sensitive information or approve fraudulent requests. According to global fraud reports, phone-based scams surged significantly between 2023 and 2024, due to large-scale data leaks, rise of VoIP-based spoofing, and AI-generated voices.
In this blog, we will explore what vishing is, how these attacks operate, real-world examples, why they are so effective, and the steps individuals and organizations can take to recognize and prevent them.
What Is Vishing?
Vishing (voice phishing) is a type of cyberattack where attackers use phone calls or voicemail messages to trick people into giving away sensitive information. Instead of relying on deceptive links or messages, vishing relies entirely on verbal communication and social manipulation.
Attackers may impersonate banks, government agencies, IT helpdesks, HR departments, or even company executives. By using publicly available information, breached datasets, and caller ID spoofing, they make their calls appear credible and urgent.
While phone scams have existed for decades, modern vishing is far more sophisticated. Attackers now use:
- VoIP technology to hide their identity
- AI-generated voice of executives or family members
- Personal info gathered from social networks, breaches, or corporate websites
- Social engineering scripts that mimic real customer support dialogues
Vishing differs from smishing and email phishing because the attacker and victim interact in real time, allowing the attacker to adapt, pressure, and manipulate individuals and organizations more effectively.
How Vishing Attacks Work
Most vishing attacks follow a structured pattern. Understanding this pattern is key to recognizing the warning signs early.
1. Reconnaissance: Studying the Victim
Attackers start by collecting personal or organizational details – often through data breaches, social media, corporate websites, or LinkedIn profiles. This aligns with the MITRE ATT&CK reconnaissance phase, where threat actors gather data to build convincing pretexts.
2. Caller ID Spoofing
Using VoIP services, attackers hide their real number and display a fake caller ID – like a bank, government agency, or even an internal company line.
3. Building a Pretext
A believable story is created to justify why they are calling. Examples include:
- Suspicious bank transactions
- Payroll discrepancies
- Tax penalties or overdue bills
- IT system outages requiring password reset
- Executive instructions for urgent transfers
These scripts are rehearsed and delivered professionally.
4. Manipulating Emotion
The attacker’s voice is their strongest tool. Through tone, urgency, fear, or authority, they push individuals toward compliance. Unlike smishing or email phishing, vishing allows fraudsters to adjust their approach based on the victim’s reactions.
5. Extracting Information or Access
The attacker eventually requests something like:
- OTPs or 2FA codes
- Banking credentials
- Remote access to devices
- Payment approvals
- Customer or employee data
6. Maintaining Pressure
Attackers often stay on the line, giving instructions step-by-step so the victim has no time to pause or verify. By the end of the call, victims may unknowingly disclose sensitive information or authorize fraudulent activity.
Common Vishing Examples
Vishing attacks appear in many forms, and each one exploits a different aspect of trust or authority.
Bank Impersonation Scams
Fraudsters pose as bank representatives, warning victims of unauthorized transactions or account security checks. Then, victims are pressured to share OTPs, card PINs, or even login credentials.
IT Helpdesk or Tech Support Fraud
Cybercriminals impersonate internal IT teams or external support services. In corporate settings, attackers ask employees to provide VPN credentials, reset passwords, or install remote-access tools.
Executive Impersonation (CEO Voice Fraud)
Attackers pose as CEOs, CFOs, or department heads. With AI voice cloning, fraudsters can replicate an executive’s tone or accent, encouraging employees to share sensitive data, confidential files, or urgently process payments.
Government or Tax Authority Calls
Victims receive threatening calls claiming unpaid taxes, legal warrants, or frozen benefits. Attackers rely heavily on fear and authority to extract information.
Insurance and Healthcare Fraud
Attackers pretend to verify policy details or patient records, prompting victims to share personal or financial data. Each scenario follows the same psychological formula: create urgency, establish authority, and push the victim toward compliance.
Why Vishing Scams Work So Well
Vishing attacks succeed because they exploit human instincts and the emotional cues embedded in voice communication. Several factors contribute to their effectiveness:
People Trust Voices More Than Text
A convincing voice creates a sense of legitimacy. Whether calm and reassuring or stern and authoritative, vocal cues shape behavior.
Authority Bias
When callers pretend to be law enforcement officers, bank managers, or senior executives, victims feel compelled to follow instructions.
AI Voice-Cloning Technology
This is one of the fastest-emerging threats. Attackers can clone a real person’s voice using leaked audio from earnings calls, speeches, or online videos – making impersonation extremely convincing.
Real-Time Adaptation
Unlike email or SMS, phone calls allow two-way interaction. Attackers can quickly adjust their approach if they sense doubt, making the manipulation more effective.
Caller ID Spoofing
Many people assume a call is safe if it appears to come from an official number – not realizing how easy it is to spoof caller IDs today. These elements come together to produce a highly effective, deeply manipulative attack vector.
Impact of Vishing Attacks
Vishing attacks cause significant harm to both individuals and organizations.
Impact on Individuals
Victims may suffer:
- Financial losses through fraudulent transactions
- Identity theft after sharing sensitive personal data
- Emotional distress from coercive conversations
- Unauthorized access to online accounts
Impact on Organizations
For businesses, vishing is especially dangerous. Criminals often target employees with access to financial systems or sensitive data.
Organizations may suffer:
- Credential theft leading to corporate breaches
- Fraudulent wire transfers (common in CEO fraud cases)
- Compromised MFA or VPN access
- Exposure of customer or employee data
- Reputational damage and compliance penalties
Recent reports indicate that over 75% of enterprises encountered vishing attempts in 2023, with attackers increasingly using LinkedIn and corporate websites to target finance, HR, and IT teams.
Phishing vs. Smishing vs. Vishing (Comparison Table)
Below is a simple comparison to clarify how these attacks differ:
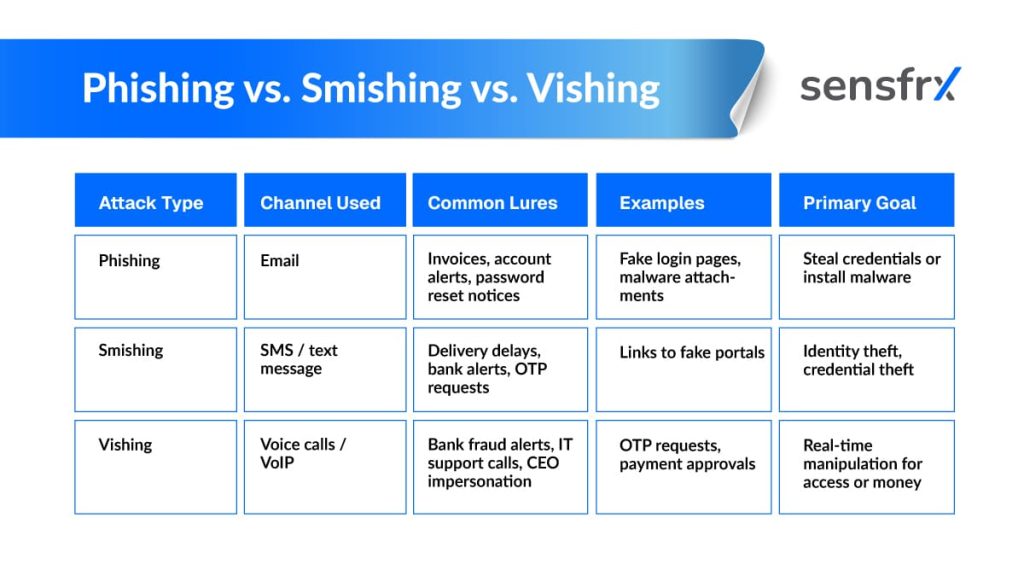
This table helps highlight that while the intent is similar, the tactics and execution vary significantly.
How to Prevent Vishing Attacks
For Individuals
- Verify the caller independently – If someone claims to be from your bank, hang up and call the official customer care number.
- Never share OTPs, PINs, or login credentials over the phone – Legitimate institutions will never ask for them.
- Be skeptical of urgent requests – Pressure and urgency are red flags.
- Use call-blocking and spam-filtering tools – Modern smartphones and carriers offer robust call-screening features.
- Limit public exposure of your phone number – Less public data gives attackers fewer starting points.
For Organizations
- Establish strict verification protocols – Finance and HR teams should have callback procedures before acting on urgent requests.
- Conduct regular vishing simulation training – Employees learn how to handle social engineering calls safely.
- Implement strong authentication mechanisms – MFA, role-based access, and privileged access controls reduce risk.
- Use VoIP security measures – Caller authentication, call analytics, and threat intelligence help identify suspicious calls.
- Define incident response processes for phone-based attacks – Security teams should know how to escalate and handle vishing incidents.
A zero-trust for phone calls mentality should be part of every organization’s culture.
What To Do If You are a Victim of Vishing
If you have fallen for a vishing attack or suspect someone attempted one:
- End the call immediately.
- Assess what information was shared.
- Contact your bank, IT team, or service provider to secure affected accounts.
- Change all relevant passwords and enable MFA.
- Document the incident and report it to the appropriate cybercrime authorities.
- Monitor your accounts for suspicious activity.
Early action significantly reduces the overall damage.
Conclusion
Vishing has evolved far beyond simple scam calls. In a world where attackers can clone voices, spoof caller IDs, and use detailed personal information to create convincing narratives, relying on instinct alone is no longer enough.
Protecting yourself – and your organization – requires a combination of awareness, verification, and strong security practices. By understanding how vishing works and staying alert during unexpected or urgent calls, you can prevent attackers from turning the human voice into a weapon.
When in doubt, hang up – and verify. Your caution is your strongest defense. To go one step further, protect your transactions & identities with Sensfrx. Book a demo today.
FAQs
Yes. Caller ID spoofing is widely used in vishing attacks, making the number appear real even when it is not.
No. Banks never request sensitive information over calls. Any such request is a strong sign of vishing.
Through data breaches, leaked databases, social media, public profiles, or automated calling tools scraping public information.
Yes. Attackers frequently target finance and IT employees to gain access to systems or authorize fraudulent transactions.
Absolutely. Attackers now use voice cloning to impersonate executives, making vishing even harder to detect.
Hang up, contact the organization through official channels, and report the incident.

