
An employee logs in from their office computer during the day, but later the same account downloads thousands of sensitive files from a server overseas. Traditional tools may overlook it since the credentials are valid, but User and Entity Behavior Analytics (UEBA) detects this anomaly instantly. With insider actions and compromised accounts involved in nearly 30% of breaches (Verizon DBIR 2024), UEBA plays a crucial role in spotting subtle risks before they cause serious damage.
What is UEBA
UEBA stands for User and Entity Behavior Analytics. It is a cybersecurity tool that utilizes artificial intelligence and machine learning to monitor the behavior of both people (users) and things (such as devices, servers, and applications) on a computer network. UEBA learns what “normal” activity looks like and then alerts you when it spots something unusual, such as someone trying to steal data or a device behaving in a suspicious way.
Difference Between UBA and UEBA
UBA and UEBA may sound familiar and, in some cases, be used interchangeably. But they are different. The table below gives an overview of both and highlights the difference:
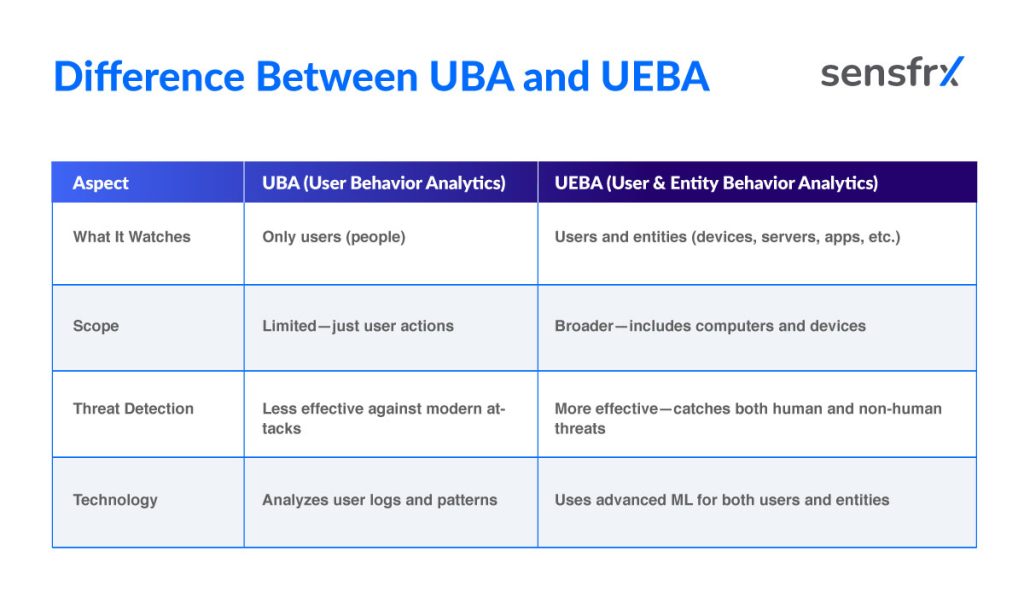
Think of UBA as focusing on what people do. UEBA expands the view to watch machines and apps, making it better at spotting clever attacks that target devices, not just people.
Why Is UEBA Critical in Today’s Cybersecurity Landscape?
- Modern threats are complex: Modern cyber threats are increasingly complex, targeting both people and devices. For example, attackers may trick employees into revealing passwords using phishing emails, or infect printers and IoT devices to steal data without detection. Traditional security tools, which focus mainly on known viruses or network anomalies, often miss these subtle attacks—especially when suspicious behavior looks normal on the surface. This is why organizations need advanced behavior analytics to spot sneaky threats that old methods overlook.
- Detects insider attacks: UEBA detects unusual actions by employees or hacked accounts—like unexpected logins or large data transfers—that traditional security tools might miss. By analyzing patterns and spotting behavior that’s out of the ordinary, UEBA helps organizations catch threats early, even when standard alarms aren’t raised.
- Automatic anomaly alerts: UEBA automatically alerts security teams when it notices unusual activity—such as a user suddenly downloading large amounts of data—by understanding what’s normal for each person or device. This early warning system helps organizations catch and address risks before they turn into serious breaches, minimizing potential damage and speeding up response.
- Better protection: UEBA helps organizations find and fix risks before they become major breaches, reducing damage and response time.
How UEBA Works: The Technology Behind Behavior Analytics
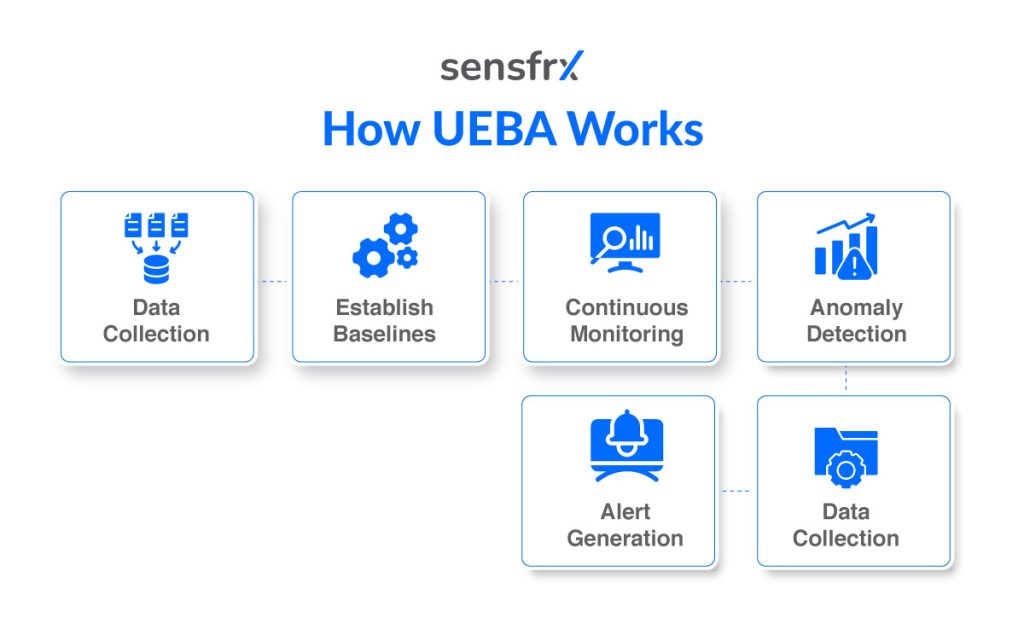
UEBA is a complex system, so let us delve deeper into getting an understanding of how it works:
Data Sources UEBA Collects From
User and Entity Behavior Analytics (UEBA) gathers data from multiple sources to build a comprehensive understanding of normal behavior, enabling the detection of cyber threats. Common data sources include:
- Users: Login records, access logs, account activity changes, and email interactions.
- Devices: Usage patterns, endpoint protection alerts, device location changes, and configuration modifications.
- Servers: System activity logs, file access logs, authentication attempts, and privilege changes.
- Applications: Application logs, API usage, transaction histories, and user permission changes.
- Network Logs: Network flow records, connection histories, failed login attempts, and abnormal traffic patterns.
By aggregating data from these sources, UEBA creates a detailed “normal” behavior profile for each user and device.
Establishing Behavior Baselines Using Machine Learning and Statistical Models
UEBA leverages machine learning and statistical modeling to analyze the collected data in order to define behavior baselines:
- The system continuously observes users and devices, learning their typical patterns such as login times, access locations, file interactions, and data volumes.
- Machine learning algorithms identify these patterns and establish personalized baselines for what normal activity looks like for each user or entity.
- Statistical models quantify what behaviors are common, rare, or anomalous relative to these baselines.
- Since baselines are customized based on roles and entity types, UEBA can detect deviations that would seem normal for others but unusual for a specific user or device.
Continuous Monitoring and Anomaly Detection in Real Time
UEBA performs real-time analysis by continuously monitoring new activity against established baselines:
- The platform detects deviations from normal behavior, flagging rare or out-of-character activities for specific users or devices.
- Significant anomalies—such as logins from unusual geographic locations or unusually large data transfers—trigger immediate alerts.
- This rapid detection enables security teams to investigate and respond promptly, helping prevent potential breaches or insider threats.
Case Example: Detecting Out-of-Pattern Data Downloads or Unusual Logins
Imagine an employee whose usual behavior is downloading several megabytes of data weekly from a single location. Suddenly:
- Their account downloads gigabytes of files, and
- They log in from a foreign country.
UEBA detects these anomalies based on deviations from the user’s established baselines.
- An alert is generated and sent to the security team.
- This actionable alert enables early investigation and response, potentially preventing a data breach or insider threat from causing serious damage.
Key Features and Capabilities of UEBA Tools
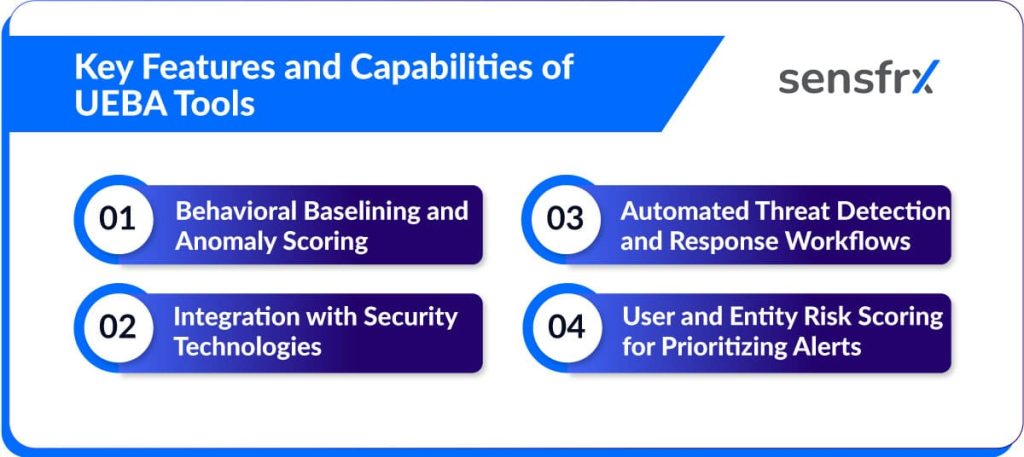
1. Behavioral Baselining and Anomaly Scoring
- UEBA tools establish behavioral baselines by analyzing typical activities and interaction patterns for users and entities (machines, applications, devices).
- They then use advanced analytics and machine learning models to assign anomaly scores when current actions deviate from these established baselines, allowing detection of suspicious or potentially malicious behavior.
2. Integration with Security Technologies
- UEBA tools are designed to integrate with other major security platforms, including:
- SIEM (Security Information and Event Management): UEBA enriches SIEM data with behavioral context for users and entities, improving detection accuracy.
- IAM (Identity and Access Management): By correlating identity data with behavioral analytics, UEBA enhances access control and threat response.
- DLP (Data Loss Prevention): UEBA supplements DLP by identifying abnormal data access, usage, or exfiltration patterns.
3. Automated Threat Detection and Response Workflows
- UEBA solutions automatically identify threats by flagging and correlating high-risk behaviors.
- They can trigger automated workflows to contain or remediate risks (e.g., locking accounts, alerting security teams, or initiating further investigation), thus reducing dwell time and improving response speed.
4. User and Entity Risk Scoring for Prioritizing Alerts
- Every user or entity is continually assigned a risk score based on current and historical behaviors.
- High-risk scores help security analysts prioritize alerts, focusing attention on the most significant threats and reducing alert fatigue by suppressing false positives.
These assembled capabilities form the backbone of modern UEBA platforms, enabling proactive and intelligent security operations by combining behavioral analytics with tight integration into broader security ecosystems.
UEBA Use Cases for Cybersecurity
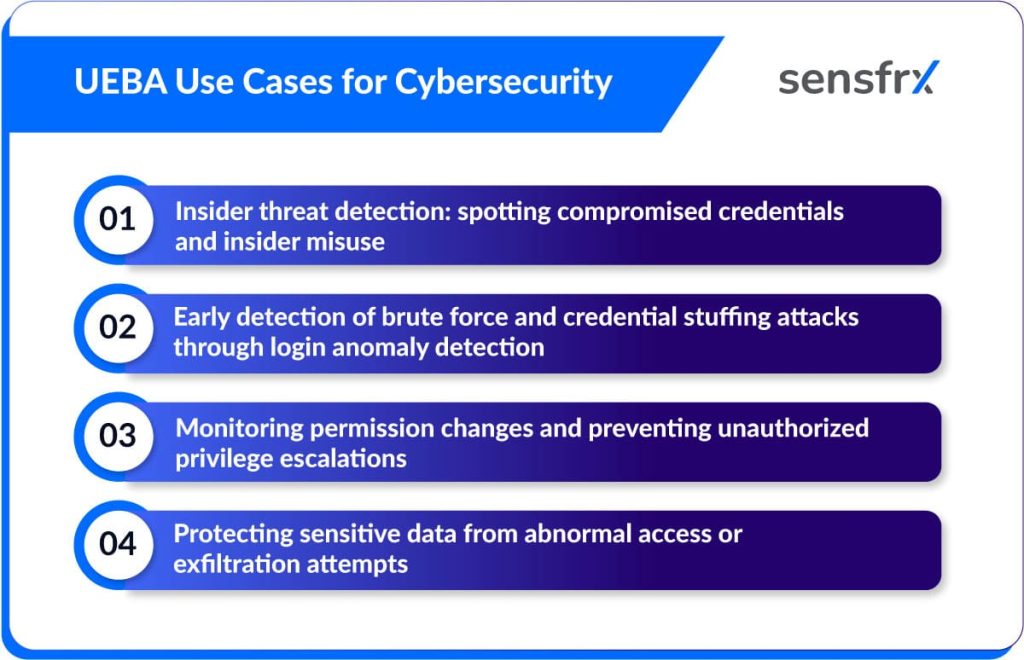
1. Insider threat detection: spotting compromised credentials and insider misuse
Insider threats don’t always come from malicious employees; sometimes legitimate accounts are compromised by external attackers. According to Verizon’s 2024 Data Breach Investigations Report, 74% of breaches involve the human element, including stolen credentials and insider misuse.
Example: A finance employee’s credentials are stolen via phishing. Attackers log in during off-hours from an unusual location and attempt wire transfers. By analyzing login behavior (time, device, geolocation), organizations can flag anomalies before funds are lost.
2. Early detection of brute force and credential stuffing attacks through login anomaly detection
Credential stuffing uses stolen username-password pairs from past breaches. Attackers automate login attempts across platforms, hoping users reuse passwords. IBM’s Cost of a Data Breach 2024 report shows credential stuffing incidents take 291 days on average to detect, costing businesses around $4.7 million.
Example: An e-commerce site sees a sudden spike of 500 failed logins in one minute, followed by successful logins from IPs linked to botnets. Detecting and blocking this early prevents mass account takeovers.
3. Monitoring permission changes and preventing unauthorized privilege escalations
Insiders or attackers with stolen credentials may try to elevate their privileges to access sensitive systems. Monitoring permission changes is critical because privilege abuse is a leading factor in insider threats.
Example: A support staff account suddenly gains “database admin” rights without a formal approval request. This is a red flag for insider misuse or compromised credentials. Implementing “just-in-time” (JIT) access and automated alerts for role changes can mitigate this.
4. Protecting sensitive data from abnormal access or exfiltration attempts
Even with valid credentials, unusual data access can indicate malicious intent. Insider data theft often involves copying large volumes of files, accessing records outside the normal scope, or attempting to exfiltrate data via email or cloud storage. Ponemon Institute’s 2023 Insider Threat Report shows 60% of insider incidents involve data theft.
Example: An employee in HR downloads hundreds of salary records overnight—far beyond their typical access pattern. Security systems using UEBA (User and Entity Behavior Analytics) can detect such anomalies and stop exfiltration before it occurs.
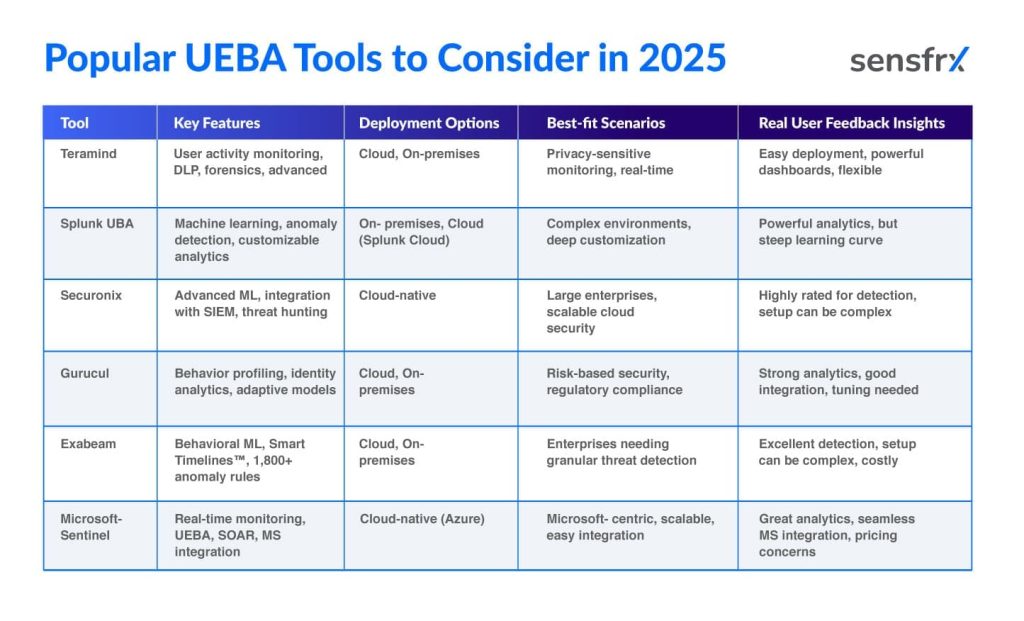
Popular UEBA Tools to Consider in 2025
Choosing the right User and Entity Behavior Analytics (UEBA) tool is crucial for strengthening an organization’s cybersecurity posture. With a growing number of advanced threats and compliance requirements, organizations need analytics solutions that offer real-time behavioral insights, anomaly detection, and seamless integrations tailored to their environments.
The following table provides a side-by-side comparison of leading UEBA tools, including Teramind, Splunk UBA, Securonix, Gurucul, Exabeam, and Microsoft Sentinel, highlighting their key features, deployment options, best-use scenarios, and genuine user feedback on performance and usability.
Best Practices for Implementing UEBA Effectively
Here’s a step-by-step breakdown of how to implement UEBA effectively according to best practices:
1. Planning Data Integration and Coverage
- Step 1: Identify all relevant data sources (e.g., identity management, endpoints, network devices, servers, applications).
- Step 2: Evaluate what data each source can provide—user activity logs, authentication events, access records, network flow data, etc.
- Step 3: Work with IT and security teams to ensure secure, compliant, and efficient data ingestion from each source.
- Step 4: Test integration to confirm data flows correctly and covers all critical segments of your IT landscape.
- Step 5: Review coverage regularly as infrastructure and applications change, adding new data sources when necessary for complete visibility.
2. Defining Clear Security Objectives Aligned with Organizational Risk Priorities
- Step 1: Convene business leaders and risk managers to list top organizational threats (e.g., insider threat, unauthorized access, data theft).
- Step 2: Translate these threats into UEBA monitoring use cases that are measurable (e.g., “Detect abnormal after-hours logins,” “Flag mass data downloads”).
- Step 3: Set specific metrics for success (frequency of detection, reduction of risk events, time to resolution).
- Step 4: Ensure security objectives align with regulatory, compliance, and business needs.
- Step 5: Periodically review and update objectives as risk priorities shift.
3. Continual Tuning of Machine Learning Models to Reduce False Positives
- Step 1: Monitor initial UEBA alerts and risk scores to identify common false positives.
- Step 2: Gather analyst feedback on alerts that proved benign, noting patterns or contexts.
- Step 3: Update the model’s baselines using recent legitimate activities—adjust peer groupings, access patterns, and thresholds.
- Step 4: Work with the vendor or platform experts to fine-tune algorithms and anomaly parameters.
- Step 5: Repeat the tuning process regularly to adapt to new work styles, technologies, and threat techniques.
4. Training Security Teams to Interpret UEBA Alerts and Respond Rapidly
- Step 1: Provide formal training about how the UEBA platform generates alerts and scores risk.
- Step 2: Use demo sessions with simulated incidents to show teams what constitutes a genuine threat versus noise.
- Step 3: Offer detailed documentation and investigation playbooks for reviewing flagged anomalies.
- Step 4: Assign roles for who acts on each type of alert to ensure rapid action and incident containment.
- Step 5: Hold regular workshops to update staff on new UEBA capabilities, rules, and alert types so the response process stays current.
Challenges and Considerations with UEBA Deployment
If you plan to deploy UEBA, then here are some of the challenges and ways to overcome them for a successful deployment:
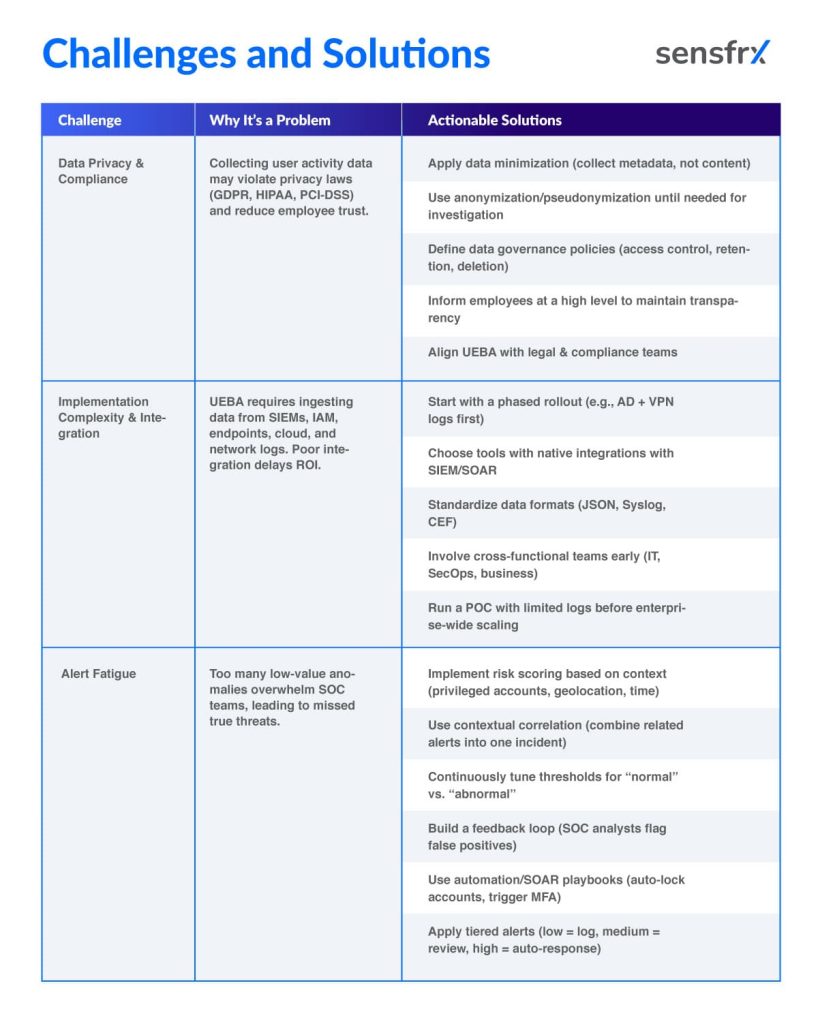
1. Managing Data Privacy & Compliance
Challenge: UEBA relies on collecting and analyzing detailed user activity (logins, emails, file access, device behavior). This can raise concerns around privacy and regulatory compliance (GDPR, HIPAA, PCI-DSS). Over-collection of personal data may also increase legal risks.
How to Overcome:
- Data Minimization: Collect only what’s essential (e.g., metadata instead of full content).
- Anonymization & Pseudonymization: Mask sensitive identifiers where possible, only unmask during investigations.
- Clear Governance: Define policies for who can access behavioral data, how long it’s stored, and when it’s deleted.
- Transparency: Inform employees about monitoring (at least at a high level) to balance trust and compliance.
- Compliance Alignment: Work with legal/HR to ensure UEBA configurations align with applicable regulations.
Actions to Take: Implement role-based access to UEBA dashboards so only authorized SOC/IR teams can see sensitive user data.
2. Overcoming Implementation Complexity and Integration Hurdles
Challenge: UEBA is not a plug-and-play solution. It requires integration with SIEMs, IAM systems, network logs, cloud apps, and endpoint monitoring. This creates complexity, especially in hybrid or multi-cloud environments.
How to Overcome:
- Start Small: Deploy UEBA in phases (e.g., begin with critical systems like Active Directory and cloud storage).
- Leverage Native Integrations: Choose a UEBA tool that integrates natively with your existing SIEM/SOAR solutions.
- Standardized Data Formats: Use logs in structured formats (JSON, Syslog, CEF) for smooth ingestion.
- Cross-team Collaboration: Involve IT, security, and business units early to align expectations and data sources.
- Automation for Scaling: Automate data collection and correlation instead of relying on manual log mapping.
Actions to take: Build a proof-of-concept (POC) with a limited dataset (e.g., VPN + AD logs) to validate effectiveness before scaling enterprise-wide.
3. Managing Alert Fatigue through Risk-Based Prioritization
Challenge: UEBA systems can generate thousands of anomalies daily. Without proper tuning, SOC teams drown in alerts, causing critical threats to be overlooked.
How to Overcome:
- Risk Scoring: Prioritize anomalies by user risk score (e.g., a privileged user logging in from a new country at 2 AM is higher risk than a standard user login attempt).
- Contextual Correlation: Combine multiple low-level anomalies into a single high-confidence incident.
- Threshold Tuning: Continuously refine thresholds for abnormal behavior (e.g., “more than 5 failed logins in 1 minute” instead of “any failed login”).
- Feedback Loop: Allow SOC analysts to mark alerts as false positives/true positives to improve detection models over time.
- Automation: Use SOAR playbooks for automatic responses (e.g., temporary account lockout, MFA challenge)
Actions to take: Set up tiered alerts:
- Tier 1: Low-risk anomalies (log for audit only).
- Tier 2: Medium-risk (SOC review).
- Tier 3: High-risk (trigger automated containment).
Here’s a “Challenges & Solutions” table for reference:
The Future of UEBA in Cybersecurity
1. Evolution Toward AI-Powered Adaptive Analytics
Traditional UEBA relies on static baselines and statistical models. The future lies in AI/ML-driven adaptive analytics that continuously learn from new data, self-adjust baselines, and adapt to evolving attack techniques. This reduces reliance on manual rule-tuning and enables detection of subtle insider threats or zero-day tactics.
Gartner predicts that by 2026, 60% of organizations will leverage AI-driven behavioral analytics to detect insider and credential-based threats.
Benefits:
- Faster and more accurate anomaly detection.
- Reduced false positives through contextual learning.
- Real-time adaptation to new threats without manual intervention.
2. Expanded Integration with Threat Intelligence and SOAR Platforms
Future UEBA platforms won’t operate in isolation. They will integrate deeply with Threat Intelligence Feeds (to correlate user behavior with known malicious IPs/domains) and SOAR (Security Orchestration, Automation, and Response) platforms for faster remediation. This means UEBA can not only detect anomalies but also enrich alerts with global intelligence and automate incident handling.
According to the Ponemon Institute, 70% of SOC teams face burnout due to repetitive manual investigations.
Benefits:
- Context-rich alerts that combine internal anomalies with external threat intelligence.
- Faster containment through SOAR automation (lock accounts, disable sessions, trigger MFA).
- Reduced workload and burnout for SOC analysts.
3. UEBA’s Role in Automated and Autonomous Response Environments
As cybersecurity shifts toward autonomous defense, UEBA will play a key role by providing behavioral context to trigger self-healing actions. Instead of waiting for analysts, future UEBA systems will automatically enforce adaptive controls like step-up authentication, temporary access restrictions, or network isolation—before threats escalate.
Gartner estimates that by 2027, 40% of large enterprises will adopt autonomous security solutions that integrate with UEBA.
Benefits:
- Near real-time containment of insider and credential-based attacks.
- Reduced mean time to detect (MTTD) and respond (MTTR).
- Business continuity is preserved without waiting for human intervention.
- Evolution toward AI-powered adaptive analytics
- Expanded integration with threat intelligence and SOAR platforms
- UEBA’s role in automated and autonomous response environments
Conclusion
User and Entity Behavior Analytics (UEBA) has become an essential component of modern cybersecurity strategies, enabling organizations to identify subtle threats, insider risks, and compromised accounts that traditional security tools often overlook. By analyzing behavioral patterns and monitoring anomalies in real time, UEBA enables security teams to anticipate, detect, and respond to attacks before they escalate.
As cyber threats become increasingly sophisticated, UEBA should be integrated into a broader, layered defense strategy rather than being treated as a standalone solution. Selecting the right UEBA platform—one that aligns with business risks, infrastructure, and operational requirements—can strengthen incident response, reduce alert fatigue, and improve overall risk visibility. This proactive approach helps organizations remain resilient in the face of emerging threats.

