
Spear phishing is a cyberattack method that uses carefully crafted emails or online messages to trick specific individuals or organizations into sharing sensitive information or performing actions that benefit attackers. Unlike generic phishing, in which attackers cast a wide net to catch random victims, spear phishing is highly targeted, personalized, and much harder to detect, making it a rising cybersecurity threat across industries.
Recent phishing research reveals that although spear phishing makes up less than 0.1% of global email traffic, it’s responsible for a staggering two-thirds of all successful security breaches. These highly targeted attacks can have devastating financial consequences: while the average phishing-related breach costs organizations nearly $5 million, losses from sophisticated spear phishing campaigns can reach $100 million or more in a single incident.
What is a Spear Phishing Attack?
A spear phishing attack is a type of targeted email scam in which a cybercriminal impersonates someone the victim trusts – such as a boss, colleague, or business contact – to trick them into clicking a malicious link, revealing their login credentials, or sending money.
Let’s take an example where an employee receives a personalized email from someone claiming to be their CEO, using a real name and signature, asking urgently for a wire transfer to a specified account for a confidential business deal.
The message uses pressure tactics, such as claiming the payment is needed immediately or that there will be negative consequences. The email looks authentic because the attacker has researched the employee’s role and the company’s hierarchy, making the request seem legitimate.
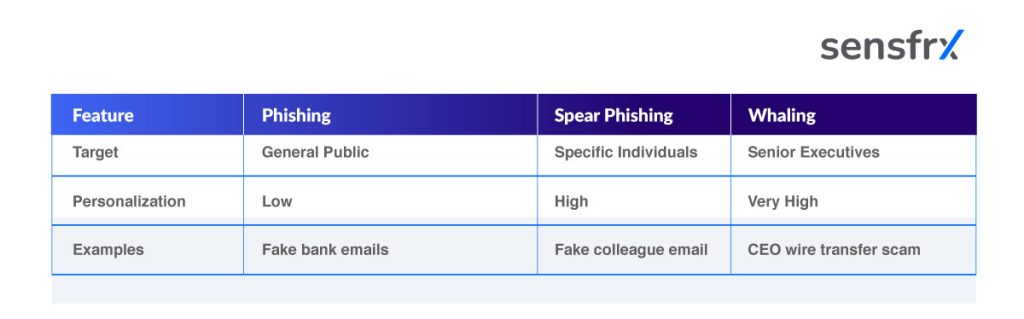
Since spear phishing might be confused with common phishing attacks or whaling, below is a quick table to understand the difference between phishing, spear phishing, and whaling:
How a Spear Phishing Attack Works (Step-by-Step)?
Let’s break down the complete process of how a spear phishing attack actually works:

Step 1: Research & Reconnaissance
Attackers gather personal and organizational details from social media, business websites, press releases, online databases, and even LinkedIn.
Example: An attacker finds an employee’s job title, recent work project, and names of colleagues from LinkedIn and Facebook profiles. This helps the attacker understand context, office relationships, and the right tone for communication.
Step 2: Crafting the Bait
Using the harvested information, attackers draft personalized emails impersonating trusted contacts – such as a manager, vendor, or IT support.
Example: The attacker writes an email to the employee pretending to be their boss. It references a real project (“Hi Priya, regarding the Q3 audit report…”), includes a familiar greeting, and may even mimic the boss’s writing style. The message asks the recipient to urgently review an attached “audit document”.
Step 3: Delivering the Email
The crafted email is sent. Because of its relevance and familiarity, the victim is more likely to click the link or open the attachment without suspicion.
Example: The employee receives the personalized email and, trusting its source, clicks a link to view “audit results” or opens an attached file. Visual cues, like a company logo and official-sounding language, make the email even more convincing.
Step 4:Exploitation
Upon clicking, credentials may be stolen, malware deployed, or money diverted to fraudulent accounts.
Clicking on the link might lead to:
- Credential theft (via a fake login page)
- Malware deployment (from a booby-trapped attachment)
- Fraudulent transactions (by sharing payment information)
Example: The attachment – actually malware – installs a keylogger, capturing login credentials. If it’s a link, it may go to a clone of the company’s Office 365 login screen; when the employee enters their password, it’s sent to the attacker.
Step 5: Execution & Persistence
With credentials or network foothold, attackers escalate their access – moving laterally, exfiltrating sensitive files, installing additional malware, or using the stolen data for financial gain.
Example: After stealing the employee’s credentials, the attacker accesses confidential client information, sends further phishing emails to colleagues (using the compromised account), or sells the login info on the dark web. Attackers may manipulate internal systems or maintain stealthy access for long periods.
Each point features targeted deception, demonstrating why spear phishing is both highly effective and hazardous for organizations and individuals.
Spear Phishing Examples
To gain a deeper understanding of spear phishing and its significant impact, let’s explore some major high-value scams, the valuable lessons they offer, and the essential measures that must be taken to prevent such attacks effectively.
RSA attack (2011)
Hackers targeted RSA employees with a malicious Excel file, leading to a breach of security tokens.
Lessons Learned & What You Can Do To Avoid Them:
- Vigilant Attachment Handling: Even seemingly routine attachments (like Excel files) pose risks. Organizations must implement strict policies: employees should never open unsolicited or suspicious-looking files, especially from unknown or unexpected sources.
Application: Automatic attachment scanning and visible warning banners for emails with unexpected attachments.
- Reduce Privileged Access Spread: Attackers moved laterally by harvesting and escalating credentials. Limiting “privilege spread” and access rights helps contain a breach if a single endpoint is compromised.
Application: Adopt least-privilege access, segment networks, and regularly review access logs and permissions.
- Real-Time Threat Detection: Traditional tools failed to react in real time. Continuous monitoring, behavioral analytics, and anomaly detection tailored for internal users provide an extra layer of protection.
Application: Deploy UEBA tools, automate alerting and response, and ensure response plans are tested and current.
- Rapid, Transparent Communication: RSA’s quick disclosure with customers helped mitigate damage and demonstrate accountability—other organizations delayed or hid details.
Application: Develop pre-approved communication plans for breach scenarios and train staff on whom to notify.
Ubiquiti Networks (2015)
Employees were tricked into wiring $40 million following spoofed emails from executives.
Lessons Learned & what you can do to avoid them:
- Multi-Step Approval & Verification: Critical financial actions should always require multiple approvals and out-of-band verification—never blindly trust urgent emails, even from apparent executives.
Application: Mandate phone or video call verification for financial requests, especially involving new accounts or large sums.
- Employee Training on Social Engineering: The success of this scam was due to social engineering, not technical hacking. Regular, scenario-based training prepares employees to recognize suspicious requests, high-pressure tactics and to escalate when in doubt.
Application: Run simulated phishing campaigns and frequent interactive workshops tailored to finance and executive assistants.
- Technical Controls for Email Authentication: Lack of advanced email authentication protocols (SPF, DKIM, DMARC) enabled easy spoofing.
Application: Implement and enforce strong email authentication for inbound and outbound messages and monitor for lookalike domains.
Google & Facebook invoice scam
Criminals posed as a hardware vendor, successfully diverting $100 million from these tech giants over several years.
Lessons Learned & what you can do to avoid them:
- Multi-Person Review: Payment and procurement processes must mandate dual review and sign-off for invoices, especially changes to payment details or new vendors.
Application: Set up workflow automation that enforces multi-level approvals for all outbound payments.
- Due Diligence on Payment Requests: Employees should verify all requests for invoice payments and bank account changes independently (never just via email).
Application: Establish a callback verification policy with documented vendor phone numbers and escalation paths.
- Ongoing Employee Security Awareness: Even sophisticated, tech-savvy employees can be deceived. Ongoing, practical training ensures finance, procurement, and IT teams are equipped to spot and block scams.
Application: Frequent refresher training, focusing on evolving tactics like domain impersonation and fake document spotting.
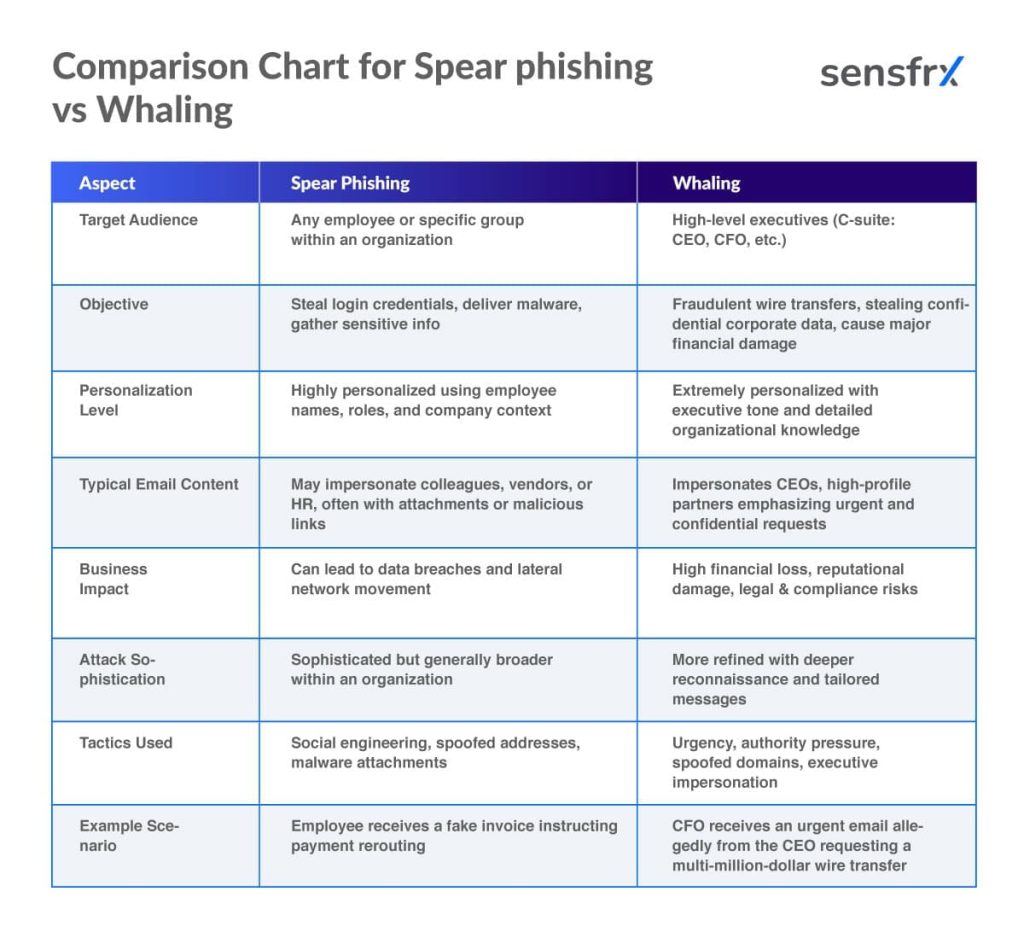
Spear Phishing vs. Whaling
Whaling is an especially targeted and sophisticated type of spear phishing that zeroes in on high-level executives, often called the C-suite (like CEOs, CFOs, and COOs), to maximize damage and financial gain. Attackers use highly refined social engineering, conducting deep background research on their targets through publicly available information such as social media profiles, company websites, and even video footage.
This research allows them to craft convincing, personalized emails or messages that impersonate trusted executives or business partners. The goal is typically to trick the victim into authorizing large financial transfers, revealing sensitive corporate data, or approving unauthorized transactions.
For example, the Australian hedge fund Levitas Capital was hit with a whaling attack where a co-founder clicked a fake Zoom meeting link, leading to malware installation, takeover of the email system, fraudulent invoice payments, and ultimately an $800,000 loss that contributed to the firm’s closure.
Spear Phishing Prevention: Best Practices for Businesses and Employees

Top Tools and Technologies to Protect Against Spear Phishing
- Email Security Gateways: Proofpoint, Mimecast
These solutions filter incoming emails at the perimeter, using sandboxing and threat intelligence to block malware, phishing, and impersonation before mail reaches user inboxes.
They help organizations neutralize sophisticated spear phishing and business email compromise attacks automatically.
- Spam Filters & AI Detection
Automated filters scan for suspicious patterns, sender reputations, and keywords, using adaptive AI models to stay ahead of emerging phishing techniques.
Modern systems like Sensfrx continually learn from new threats, reducing false positives and catching attacks that evade traditional rules. Sensfrx enhances this category by analyzing behavior, device fingerprints, email content, and sender details with AI to identify phishing and spam in real time, adapting quickly to new attack patterns and sharply reducing false positives.
Modern systems like Sensfrx continually learn from new threats, blocking advanced fraud attempts often before they reach users, and can be integrated with existing email platforms for seamless protection.
- Multi-Factor Authentication (MFA)
MFA requires users to verify logins with something beyond a password, such as a code, token, or biometric check. Even if passwords are stolen via phishing, MFA blocks unauthorized access by demanding a second proof of identity.
- DMARC, DKIM, SPF
These protocols authenticate sender identities and protect against email spoofing by verifying legitimate sources before emails are delivered. When configured correctly, they reduce impersonation risk and help filter fraudulent messages out of the mailstream.
- Security Awareness Platforms: KnowBe4, Cofense
Specialized platforms deliver ongoing training and simulated phishing to teach employees how to recognize, avoid, and report suspicious email activity.
They build a proactive security culture, reducing human error and strengthening organizational defenses against spear phishing.
How to Respond if You Fall Victim to a Spear Phishing Attack
Here is an elaborated explanation for each response step if a spear phishing attack occurs:
Immediate Steps
1. Report the Incident to IT/Security Teams
- Quickly alerting the organization’s IT or cybersecurity team ensures early containment. It enables experts to assess the scope, isolate affected systems, and prevent further spread or damage.
- Timely reporting can stop attackers from escalating access or exploiting compromised credentials further.
2. Reset All Credentials
- Changing passwords and access tokens immediately mitigates the risk of continued unauthorized use. Resetting applies to the victim’s email, corporate accounts, cloud services, and any related systems.
- Strong, unique passwords combined with multi-factor authentication (MFA) minimize the chances of repeated compromise.
3. Run Endpoint Scans to Detect and Remove Malware
- Comprehensive scans on infected machines identify hidden malware, trojans, or keyloggers planted during the attack. Early detection allows rapid removal and reduces risk of data exfiltration or continued backdoor presence.
- Antivirus, endpoint detection and response (EDR), or specialized anti-malware tools should be used with up-to-date definitions.
Long-Term Response
1. Review and Strengthen Incident Response Policies
- Organizations must evaluate lessons learned to update their incident response (IR) plans, defining clearer escalation paths, roles, and responsibilities for future incidents.
- Regular IR plan drills and audits ensure readiness and improve response speed.
2. Educate Employees on Recognizing Phishing
- Broadening security awareness training with specific spear phishing scenarios helps employees spot subtle red flags and suspicious behaviors.
- Frequent simulated phishing exercises boost vigilance and foster a security-first culture.
3. Analyze Attack Vectors and Methods
- Incident analysis uncovers phishing techniques, exploited vulnerabilities, and process gaps. This intelligence allows targeted improvements in technical controls and user training.
- This may include stronger email filtering, enhanced threat intelligence, or revised vendor verification steps.
4. Support Affected Users
- Victims may require guidance, counseling, or technical assistance to recover from identity theft or privacy breaches stemming from the attack.
- Providing clear communication, reassurance, and resources helps maintain user confidence and mitigates operational disruption.
Conclusion
Heightened awareness and reliable security tools are fundamental for defending against spear phishing and other targeted cyber threats. Even the most sophisticated technical defenses can be bypassed when users, employees, or organizations let down their guard. Combining proactive habits with specialized technology is the gold standard for protection.
Regular training, vigilant verification of senders and URLs, and rapid incident response should become everyday practices in every organization’s and individual’s digital life.
Adopt robust spear phishing prevention strategies and reinforce your security framework before it’s too late.
For comprehensive, AI-powered protection, Try Sensfrx, a platform designed to actively scan emails, detect phishing attempts, and block malicious domains using cutting-edge machine learning. Sensfrx delivers real-time alerts, automated threat removal, and seamless integration with your existing systems – defending users and enterprises from evolving social engineering attacks.
Get started with Sensfrx today to secure your people, data, and reputation from the next spear phishing threat before it can strike.
FAQ’s
Spear phishing is a targeted cyberattack where attackers send personalized, deceptive messages to trick victims into revealing sensitive information or clicking malicious links. Unlike generic phishing, it focuses on specific individuals or organizations.
Regular phishing casts a wide net with generic emails, while spear phishing is highly targeted and tailored using personal or organizational details, making it harder to detect.
Warning signs include unusual sender addresses, urgent requests for sensitive data, suspicious links or attachments, slight typos, and a tone that feels “off” compared to normal communication.
Immediately change compromised passwords, enable MFA, disconnect the affected device, report the incident to your IT/security team, and inform your bank or service provider if financial data was exposed.

