
Picture this: You open your store dashboard in the morning and find dozens of fake orders made overnight through real customer accounts. Your website wasn’t hacked in the usual way. Instead, attackers used stolen usernames and passwords from other breaches to log in. That’s credential stuffing.
IBM’s 2024 Cost of a Data Breach report shows that these attacks take the longest to detect, with an average of 291 days, and cost companies about $4.7 million per breach.
The problem is only getting worse. Bots are becoming more sophisticated, CAPTCHA is no longer a strong barrier, and stolen credentials are sold in massive quantities on underground markets. This isn’t just a small nuisance anymore, it’s a major threat that can drain revenue, erode customer trust, and damage your brand’s reputation.
To understand how to stop it, we first need to look at what’s happening behind the scenes—how credential stuffing works, why it’s on the rise, and the weaknesses attackers exploit.
What Is Credential Stuffing?
Credential stuffing is an automated cyberattack where attackers use lists of stolen usernames and passwords—often acquired from previous data breaches—to attempt to gain unauthorized access to user accounts on unrelated websites or services. Instead of guessing passwords (like a brute-force attack), credential stuffing simply tries known credential pairs, often at a massive scale, using bots or scripts.
According to a study by Keeper Security, 44% of surveyed employees reported reusing the same password across both their personal and work accounts. Credential stuffing is so widespread and effective because it exploits people’s tendency to reuse passwords and leverages the massive volume of leaked data now available from years of breaches. Also, credential stuffing is cost-effective for attackers: even though the success rate is often under 2%, large-scale automation means a small percentage of successful logins yields thousands of account takeovers.
Brute Force vs Credential Stuffing vs Password Spraying
People often confuse credential attacks with brute force and password spraying. While these attacks may seem similar at first glance, brute force, credential stuffing, and password spraying use distinct methods to compromise accounts, and understanding the differences is key to defending against them.
Brute Force Attacks
Brute force is when an attacker tries to guess a password by systematically testing many combinations, like trying every possible key until one works. The attacker does not need to have any prior information; they just try over and over. In 2025, about 51% of hackers still used brute force attacks due to cloud vulnerabilities and easy-to-guess admin usernames.
Example: Someone tries “password1”, “password2”, “password3″… all the way up to “password999999” until they get in. A simple automated tool might test millions of possible passwords for a single user account.
Why It Happens: Weak or common passwords (“123456”, “password”) make brute force easier and faster. Attackers can use software to automate this process.
Credential Stuffing
In credential stuffing, attackers use real username-password pairs stolen in previous data breaches. They try these known credentials on multiple websites, hoping users reused passwords elsewhere. 81% of people reuse passwords on multiple sites. Credential stuffing can have up to a 2% success rate, meaning 1 million credentials might hijack 20,000+ accounts.
Example: If a hacker steals 1 million usernames and passwords from an old video game site, they use bots to try those same details on banking, shopping, or email sites. Even with a success rate of 1–2%, this could mean thousands of hijacked accounts.
Why It Happens: Credential stuffing thrives on a simple but dangerous habit—password reuse. Many people use the same password for multiple websites or services, often for convenience. When a data breach at one company exposes usernames and passwords, those credentials are sold, shared, or traded on underground forums and dark web marketplaces. Attackers then take these stolen username-password pairs—sometimes in the billions and use automated tools (often called “bots”) to try them on other platforms.
Password Spraying
Password spraying is when attackers take a single (or small set of) common password like “Password123″—and try it on many different accounts, instead of many passwords for one account. In 2022, government agencies identified password spraying as a popular attack among state-sponsored hackers.
Example: An attacker might test “Welcome2024” as the password for every employee account at a company. Then, after a while to avoid a lockout, they try “Summer2024” on all the accounts
Why It Happens: Many people use weak or common passwords. By rotating through accounts instead of passwords, attackers avoid automatic lockouts that trigger after multiple failed attempts on a single account.
Below is a side-by-side comparison of each of the attack types:
| Aspect | Brute Force | Credential Stuffing | Password Spraying |
| How It Works | Tries many passwords for 1 account | Tries many real password–username pairs (from breaches) on multiple sites | Tries one or a few common passwords on many accounts |
| Needs Prior Data? | No | Yes (needs stolen credentials) | No, just needs usernames |
| Target | Any account | Accounts with reused passwords | Multiple accounts |
| Succeeds Because | Weak/simple passwords | Password reuse across sites | Common passwords used |
| Example | “aaa”, “aab”, “aac”, … | Using known pairs from the old breach on the new sites | “Password1” was tried for every employee account |
| Key Prevention | Use strong, unique passwords | Use unique passwords per site, enable MFA | Avoid default/common passwords; lock accounts after failed attempts |
| Typical Success Rate | Very low for strong passwords | 0.1–2% (but thousands of accounts per million tried) | Depends on password strength and account lockout policies. |
How Credential Stuffing Works – Step by Step
Credential stuffing attacks follow a series of automated steps that make them dangerous and effective. Below are the steps involved:
- Source of leaked credentials
- Use of bots for automation
- Login attempts at scale
- Indicators of success
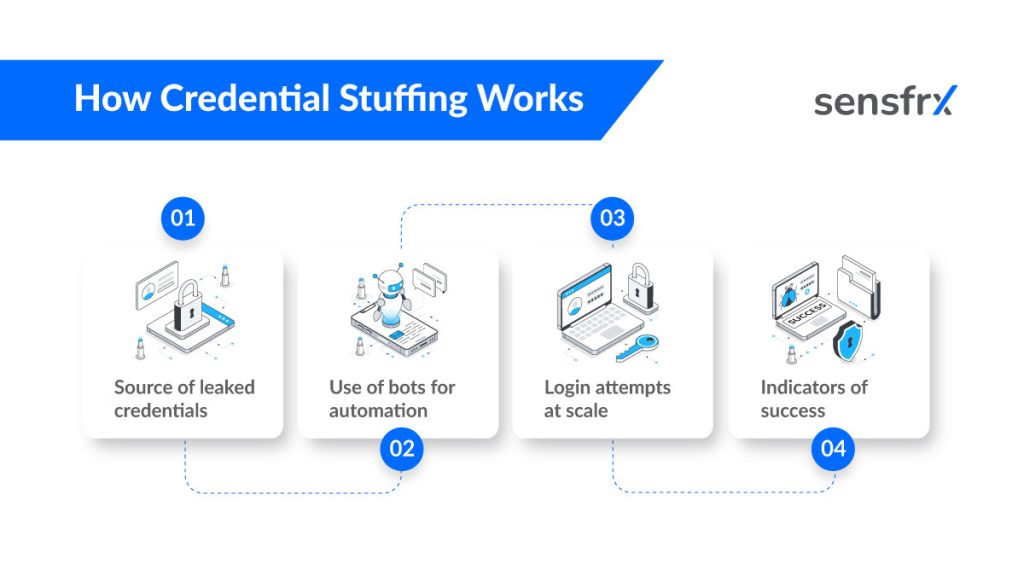
1. Source of Leaked Credentials
- Attackers obtain username and password pairs primarily from data breaches. Over 15 billion stolen credentials from around 100,000 breaches are circulating on cybercrime forums and dark web marketplaces.
- Credentials can also be gathered through phishing campaigns or malware (like keyloggers) that steal login details.
- These stolen credentials—sometimes called “combolists”—are bought, sold, or shared widely, creating a massive pool of attack data.
2. Use of Bots for Automation
- Attackers load large credential lists into specialized software or bots, such as OpenBullet, Sentry MBA, or SNIPR, which automate login attempts across multiple websites simultaneously.
- Bots rotate IP addresses and use proxies or botnets (networks of compromised devices) to mask their activity and evade rate limits or IP blocks.
- Modern bots can even mimic human behavior, bypass simple CAPTCHAs, and evade detection by blending with normal traffic patterns.
3. Login Attempts at Scale
- Bots attempt millions of login tries by injecting stolen credentials into login forms or APIs. Timing, geolocation, and device types are often varied to avoid raising suspicion.
- To avoid triggering account lockouts, bots typically try one credential set per account before moving on to the next.
- Despite low success rates of about 0.2% to 2%, the volume makes it possible to take over thousands or even millions of accounts. For instance, trying 1 million credential pairs might yield 2,000 to 20,000 hijacked accounts.
4. Indicators of Success
- The bots log valid credentials that allow successful logins, called “hits.”
- Attackers exploit these access points to steal data, commit financial fraud, or sell the compromised accounts.
- Security teams may detect attacks by unusual spikes in failed logins, login attempts from diverse or new IPs, login surges during off-hours, or sudden drops in the ratio of successful to failed logins.
- Behavioral analytics, device fingerprinting, and anomaly detection are now key to early identification and mitigation of these attacks.
Real-World Impacts of Credential Stuffing
Credential stuffing continues to be a major cybersecurity threat in 2025, causing significant financial loss, operational disruption, and reputation damage across various industries. Attackers exploit stolen credentials and users’ poor password hygiene to hijack accounts, steal data, and commit fraud.
Below is an overview of its impact on some of the most commonly targeted industries:
Industries Commonly Targeted
- E-commerce
- Financial services
- Media and streaming
- Healthcare
E-commerce
Credential stuffing accounts for up to 91% of login traffic targeting e-commerce sites during peak seasons, making online retailers particularly vulnerable. Attackers exploit reused passwords to access customer accounts containing payment details, purchase history, and loyalty rewards. In July 2022, The North Face experienced a credential stuffing attack, exposing nearly 195,000 user accounts.
These attacks not only cause direct financial loss but also increase customer support workload due to account lockouts and reset requests, while damaging consumer trust and brand reputation. Globally, losses from credential stuffing attacks in e-commerce are projected to reach $17 billion by 2024, driven by fraudulent purchases and expensive remediation efforts.
Financial Services
Banks and credit unions are prime targets due to the high value of money and sensitive data they hold. Credential stuffing enables unauthorized transfers, fraudulent transactions, and theft of personal information. The average cost per credential stuffing breach in financial services can run into millions of dollars, combining direct fraud, regulatory fines, and reputational damage.
The scale and automation of these attacks complicate defense, forcing financial institutions to invest heavily in multi-factor authentication (MFA) and machine learning-based threat detection to keep pace with evolving threats.
Financial institutions see constant attack campaigns that test thousands of stolen credential sets per second, exploiting common password reuse and weak authentication policies.
Media and Streaming
The media industry faces intense credential stuffing pressure, with billions of attack attempts recorded. Streaming services are targeted not only for account takeovers but also for unauthorized access to paid content, leading to revenue loss and piracy.
Akamai reported over 17 billion credential stuffing incidents targeting media from 2018-2019, making it one of the highest attacked verticals.
Popular platforms like Spotify have suffered multi-year bouts of credential stuffing attacks, sometimes affecting hundreds of thousands of accounts, resulting in unauthorized account changes and fraudulent access.
Healthcare
Healthcare is among the most attacked industries with credential stuffing, primarily due to the high sensitivity of personal health information and the sector’s historically weak cybersecurity defenses. These credentials can be used to commit medical fraud, obtain prescription drugs, file false insurance claims, steal identities, or be sold on the dark web at premium prices.
In 2024 alone, more than 3.2 billion healthcare-related credentials were compromised globally, marking a 33% increase from the prior year.
The table below outlines the primary risks for each industry and the ways attackers can profit from accounts compromised via credential stuffing.
| Sector | How Stolen Accounts Are Used |
| Ecommerce | – Abuse refund systems – Steal loyalty points/gift cards- Place fraudulent orders- Harvest personal data for resale- Resell compromised accounts/data on black markets |
| Healthcare | – Exfiltrate sensitive medical/insurance data for resale or extortion- Commit insurance fraud- Launch targeted phishing campaigns using leaked PII (patient info)- Medical identity theft |
| Financial Institutions | – Unauthorized transfers of funds- Identity theft leading to new credit or loan applications- Money laundering using trusted accounts- Abuse loyalty points or open new credit accounts |
| Media & Streaming | – Sell “shared” premium accounts ( Netflix, Spotify, etc. ) on dark web/black markets- Resell compromised accounts- Access and resell restricted or paid content |
How to Detect a Credential Stuffing Attack
When credential stuffing or similar attacks happen, security teams look for unusual signs—called indicators of compromise (IoCs)—that reveal potential account takeovers or cyber intrusions. Here are some common, easy-to-understand examples of such indicators:
Indicators of Compromise
- Unusual login patterns
- Spikes in failed login attempts
- Logins from odd geographies
- Device/browser fingerprint mismatches
1. Unusual Login Patterns
A user who typically logs in once or twice a day suddenly has dozens of login attempts within a short period. Or logins occur at strange times, like in the middle of the night, which is unusual for that user.
What it means: It might indicate that automated bots or attackers are trying many credentials and that may trigger many rapid login attempts, far above normal user behavior.
2. Spikes in Failed Login Attempts
A website’s login system suddenly sees thousands of failed logins in an hour from many different accounts.
What it means: This spike often signals a credential stuffing attack where bots test lots of stolen username-password pairs, causing many failed attempts before some succeed.
3. Logins from Odd Geographies
A user based in India normally logs in from Mumbai, but suddenly their account logs in from Europe or South America within a short span.
What it means: Attackers leveraging proxies or botnets from different locations try to mask their identity; such geographic anomalies can point toward account compromise.
4. Device/Browser Fingerprint Mismatches
A user’s account is usually accessed from a specific device and browser (e.g., Chrome on a Windows laptop), but suddenly the account is accessed from unfamiliar devices or browsers (e.g., a mobile phone using Firefox or an unusual operating system).
What it means: Changes in device or browser fingerprints during login attempts can indicate unauthorized access by someone other than the legitimate user.
Tools and Techniques for Detection
Early detection of cyber threats is crucial for reducing potential damage and ensuring swift response. Leveraging tools like SIEM, behavioral analytics, and deception techniques greatly enhances an organization’s ability to identify and neutralize attacks.
Let’s deep dive into the major tools and techniques you can implement for for effective detection:
SIEM (Security information and event management) Pattern Correlation
Security information and event management tools are specialized cybersecurity solutions that collect, aggregate, and analyze security data, including log files and event records, from across an organization’s IT environment to detect, investigate, and respond to threats in real-time.
SIEM pattern correlation means linking different security events together to spot signs of an attack that single events might miss. It helps ‘connect the dots’ so suspicious activity is caught faster and with fewer false alerts.
Imagine a company’s SIEM system notices several failed login attempts on a user account from different locations within a few minutes. Alone, these failed attempts might not trigger a serious alert. But then, the system detects a successful login from one of those locations shortly after. Using pattern correlation, the SIEM links these events together and raises a high-priority alert because this pattern matches a common attack method called a “brute force” or “credential stuffing” attack. This way, the security team can respond quickly to stop potential unauthorized access before damage occurs.
Common features of SIEM tools include:
- Real-time monitoring and behavioral analytics.
- Automated alerts and incident response workflows.
- Data aggregation and event correlation from diverse sources, such as network devices, servers, applications, and security hardware.
- Threat intelligence integration and advanced analytics to identify complex attack patterns.
- Compliance reporting and audit support
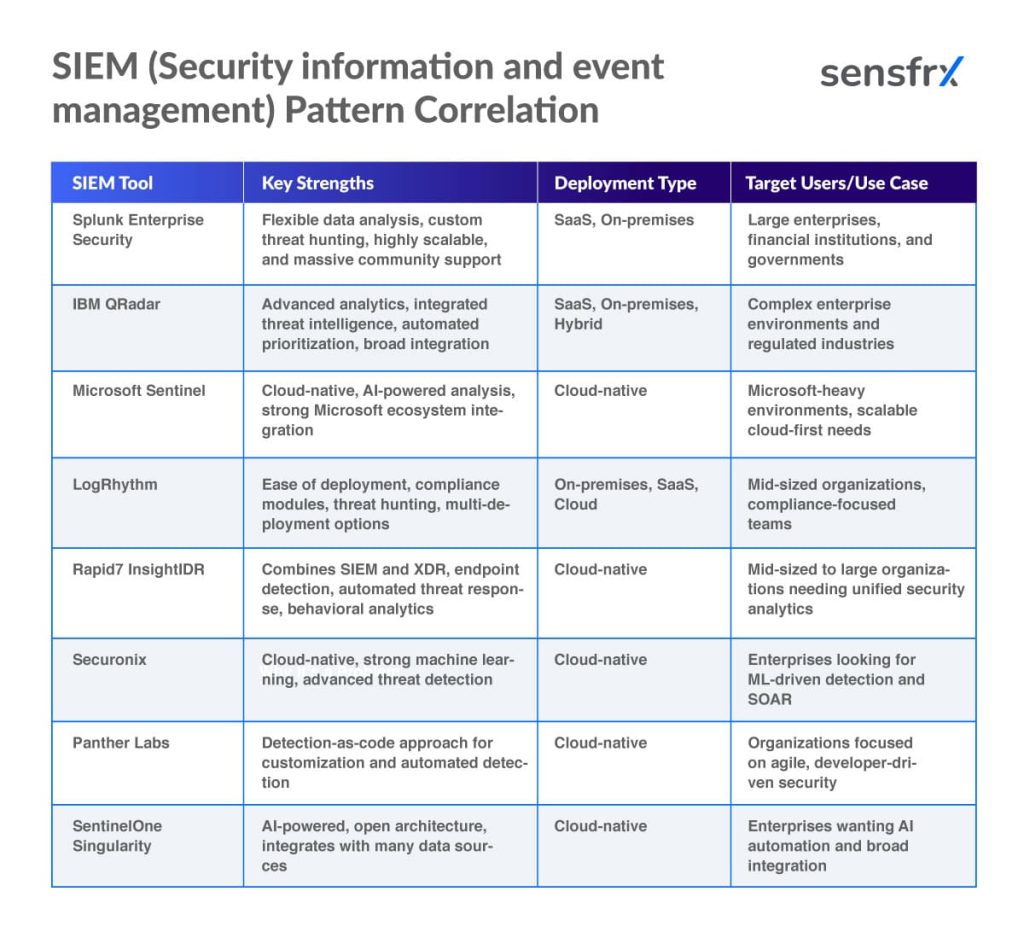
Below are the examples of prominent SIEM platforms in 2025, their key strengths, and target users:
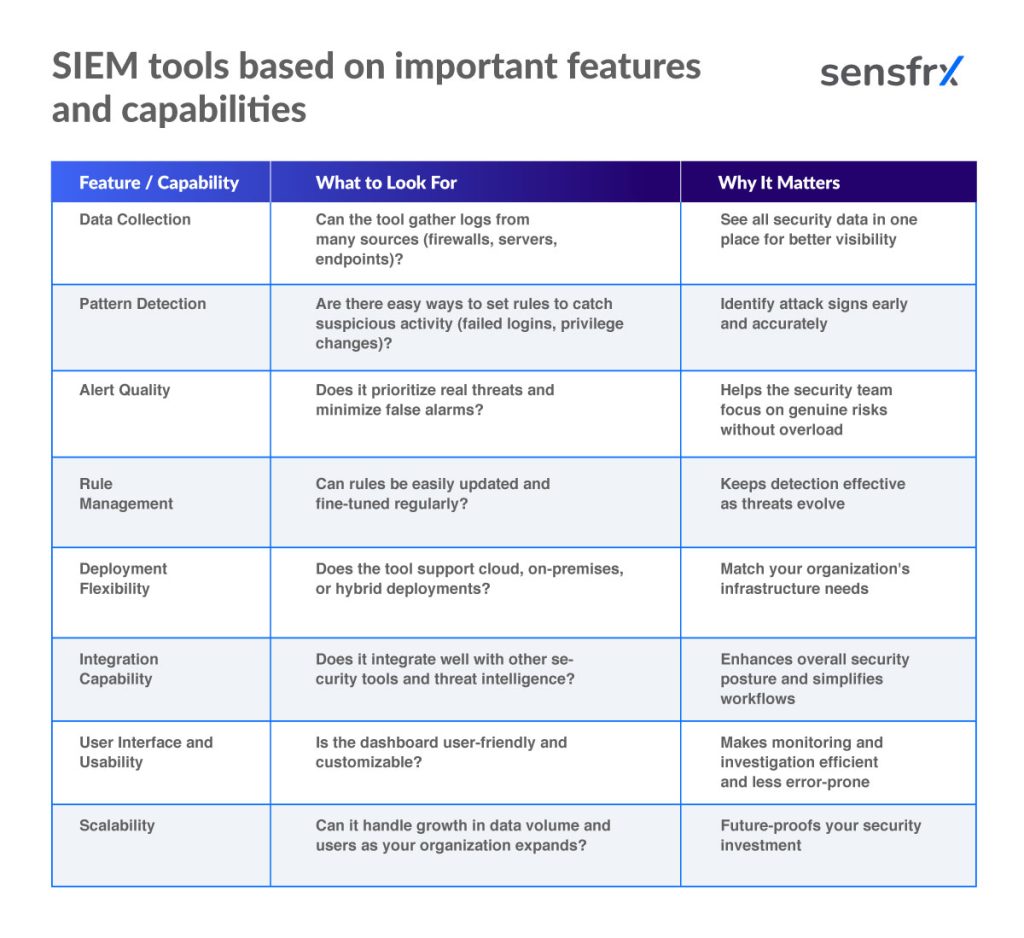
Below is a visually clear comparison checklist to help quickly evaluate SIEM tools based on important features and capabilities:
Behavioral Analytics
Behavioral analytics uses machine learning and AI tools to establish patterns of normal user behavior—such as typical login times, locations, devices, and accessed resources—and then monitors for deviations from these patterns. When something unusual happens, like a login from an unexpected country, multiple failed logins, or rapid access to sensitive data, behavioral analytics flags it for immediate investigation or automatic response.
How it Helps Prevent Credential Stuffing: Over 80% of web application breaches are caused by stolen or reused credentials, which are also frequently used in credential stuffing attacks, making this a leading cause of security incidents globally. Behavioral analytics can detect the automation behind these attacks by identifying abnormal login velocity, unusual device fingerprints, or inconsistent user access patterns—triggering alerts or multi factor authentication challenges before attackers gain access.
Why Behavioral Analytics Is Essential: Traditional defenses like passwords alone are insufficient, especially given the rise of AI-assisted brute force tools and remote/hybrid work, increasing attack surfaces. Behavioral analytics adds a dynamic, context-aware layer of defense by continuously learning user behavior and enabling security teams to spot and stop attacks early—including subtle signs of credential stuffing—reducing false positives and improving response speed.
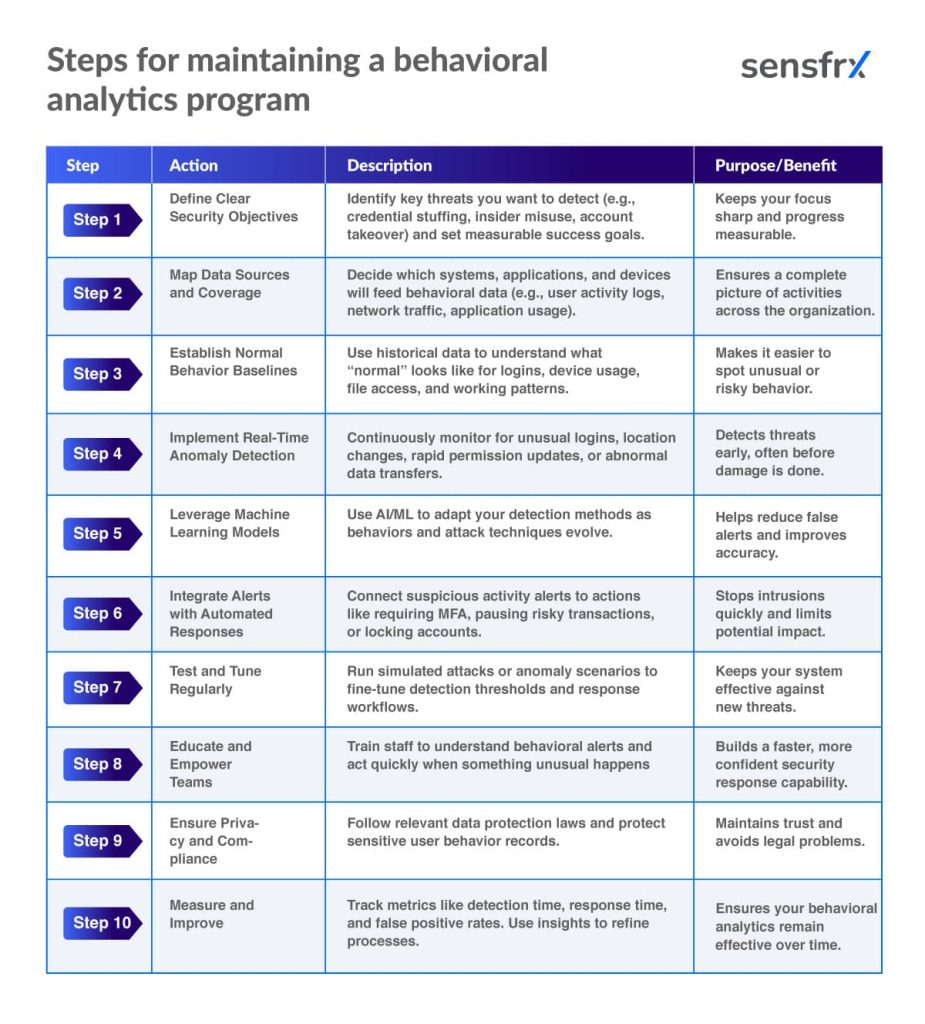
The table below outlines key steps, from setting clear objectives to continuous improvement, that will help you design, implement, and maintain a behavioral analytics program that works as intended.
Velocity Checks and Honeypots
Velocity checks monitor the speed and frequency of certain user or system actions to detect potential malicious activity. For example, logging in from two distant locations within a short time (“impossible travel”), rapid file downloads or transfers, or quick changes to user privileges can indicate compromised accounts or insider threats.
Actionable Tips:
- Define thresholds for suspicious velocity, such as more than one login from geographically distant locations within 30 minutes, or privilege escalations occurring more than twice in a day.
- Use analytics tools to automatically flag or alert on these velocity anomalies in real time.
- Combine velocity checks with other context, such as device type or login behavior, to reduce false positives.
- Continuously tune thresholds based on normal organizational activity patterns and emerging threat trends.
Honeypots
Honeypots are decoy systems, files, or services designed to appear as attractive targets for attackers. They serve as early warning traps, attracting attackers who perform reconnaissance or exploitation techniques. Monitoring interactions with honeypots allows organizations to identify attack attempts before real assets are compromised.
Actionable Tips:
- Deploy multiple types of honeypots mimicking various critical assets (servers, databases, admin consoles, files).
- Ensure honeypots generate detailed logs of attacker activities, including IP addresses, tools used, and tactics.
- Routinely update and rotate honeypot assets and their configurations to prevent attackers from identifying them easily.
- Use deception technology to make honeypots blend seamlessly into the environment without raising suspicion.
Benefits of Combining These Techniques
Using velocity checks and honeypots together empowers organizations to:
- Proactively detect suspicious behaviors that may otherwise go unnoticed.
- Gain early visibility into attacker tactics before real damage occurs.
- Prioritize and respond faster to genuine threats, reducing the time it takes to contain incidents.
Mitigating Credential Stuffing Attacks
Credential stuffing attacks, driven by stolen or leaked credentials, pose a significant cybersecurity risk worldwide. Effective mitigation requires a multi-layered approach combining front-end controls, robust credential hygiene, and advanced bot mitigation solutions.
Let’s discuss each one in detail:
Front-End Controls
Front-end controls act as the first line of defense, preventing many attacks before they even reach your systems. These safeguards are implemented directly in the user interface to block suspicious actions and guide safe behavior.
It includes:
- CAPTCHA and Rate Limiting: Deploy CAPTCHA challenges on login pages to differentiate between human users and automated bots. Combine this with rate limiting to restrict the number of login attempts from a single IP or device within a defined time window.
For example, setting thresholds to block more than five failed login attempts per minute significantly reduces automated attack success. Cloudflare’s 2023 data shows that rate limiting alone blocks 78% of credential stuffing attempts. When layered with bot detection (e.g., reCAPTCHA), efficacy exceeds 90% as per a report published by Akamai in 2022.
- Device Fingerprinting: Use device fingerprinting technologies to recognize devices based on attributes like browser type, OS, IP address, and configurations. This helps identify when an unusual or new device attempts to access an account, triggering additional verification steps. For instance, monitoring login attempts from devices never seen before can flag potential attacks before account takeover occurs.
- Behavioral Biometrics: Behavioral biometrics analyzes how users interact with their devices (typing speed, mouse movements, touch patterns) to build unique user profiles. Any deviation from these patterns during login or transactions can prompt adaptive authentication or block access.
Credential Hygiene
Credential hygiene refers to the practice of creating, storing, and managing passwords securely to reduce the risk of account compromise. Good hygiene includes using strong, unique passwords and updating them regularly.
Below are some of the options that can be implemented:
- Enforcing Strong Password Policies: Require users to create complex passwords that include a mix of uppercase and lowercase letters, numbers, and symbols. Implement password expiration policies and discourage the reuse of passwords across multiple accounts. According to NIST guidelines, longer passphrases are both more secure and user-friendly. As per a report, Strong passwords are more effective than most people realize. A complex 12-character password takes 62 trillion times longer to crack than a 6-character password.
- Blocking Known Breached Credentials: Integrate real-time checks against publicly available databases of leaked credentials (e.g., Have I Been Pwned) to prevent users from registering or logging in with compromised passwords. Blocking known breached credentials can reduce risk by preventing attackers from exploiting reused or leaked passwords.
- Mandatory Multi-Factor Authentication (MFA): Enforce MFA for all users, especially for sensitive accounts and high-risk transactions. MFA adds an extra layer of security beyond passwords, rendering credential stuffing attempts much less effective. Data from Jumpcloud shows organizations with mandatory MFA experience 99.9% fewer account takeovers from stolen credentials.
Bot Mitigation Solutions
Bot mitigation solutions help detect, block, and manage malicious automated traffic before it can exploit vulnerabilities. Some of the ways to mitigate bot attacks are:
- Web Application Firewalls (WAF): Deploy WAFs to filter, monitor, and block malicious traffic, including bot-driven credential stuffing attempts. WAFs can identify attack patterns and block suspicious IP addresses or geographies.
- Bot Management Platforms: Use specialized bot management solutions that use AI and machine learning to distinguish sophisticated bots from legitimate users. These platforms provide visibility into bot traffic, enabling granular control, such as blocking, rate limiting, or issuing progressive challenges.
- Progressive Challenges: Implement progressive challenges that escalate based on risk indicators—starting with invisible checks, then CAPTCHAs, and eventually out-of-band verification if suspicious activity persists. This adaptive approach minimizes user friction while effectively stopping bots.
Best Practices for Organizations
Let us now discuss what best practices organizations can follow to protect against credential stuffing attacks to minimize the damage.
Preventive Measures
Prevention is the most cost-effective defense against credential stuffing. Implementing the measures below can significantly reduce the chances of a successful attack.
1. Monitoring Credential Dump Forums
Continuously monitor the dark web and open forums where stolen credentials are traded. Utilize threat intelligence services, such as Flashpoint or Recorded Future, that actively scan over 25,000 illicit sites for leaked data. For instance, if your company begins monitoring credential dumps and finds that 2,000 of its users’ credentials have appeared in leak forums, you can instantly enable rapid forced password resets and avert account takeover.
According to new data published by an external risk management and threat intelligence firm, Cyberint leaked credentials in 2025 have surged by 160% compared to last year.
2. Credential Stuffing Red Team Simulations
Regularly run simulated credential stuffing attacks using tools like Open Web Application Security Project (OWASP) ZAP or custom scripts to assess your defense. In a 2024 survey, 82% of enterprises conducting red team simulations discovered overlooked vulnerabilities in their login flows, such as weak rate limits and a lack of breached password checks.
Companies performing annual attack simulations are 2.5 times less likely to suffer major account compromise incidents compared to those that do not test their systems proactively.
3. Employee Training and Access Segregation
Train employees to recognize phishing tactics and enforce least-privilege access. For example, Kaiser Permanente reduced phishing clicks by 70% after quarterly training, while CISA documented a 40% drop in credential misuse at healthcare providers using access segregation.
4. Incident Response Readiness
Being prepared before an attack strikes can make all the difference in minimizing damage. Incident response readiness ensures your team can detect, contain, and recover from security incidents quickly and effectively.
Response Playbook for Credential Stuffing
- Build a detailed credential stuffing playbook with step-by-step procedures that should include:
- How to detect credential stuffing attempts (monitor login anomalies, velocity checks).
- Immediate automated actions (lock affected accounts, force password resets).
- Rapid notification process for users and internal stakeholders.
- Clear escalation and handoff to incident response teams.
- Rehearse the playbook regularly via simulated credential stuffing attacks to expose gaps
For example, after refining their credential-stuffing playbook through quarterly simulations, Twilio contained a 2023 attack within 12 hours by automating account lockouts and SMS alerts.
Notification Obligations (e.g., GDPR, CCPA)
Ensure notification procedures comply with regulations like GDPR and CCPA.
- Map out all data breach notification laws that apply (such as GDPR, CCPA).
- Incorporate notification deadlines into your playbook—ensure affected users and regulators (when required) are contacted within set timelines (e.g., GDPR requires notification within 72 hours).
- Automate breach notifications where possible for speed and auditability.
- Consult legal counsel to review and refresh notification procedures every six months to remain compliant with evolving regulations.
User Communication Templates
Prepare and regularly update email and in-app notification templates for user communication following a credential compromise. For example, Chase Bank’s templated alerts during a 2022 credential attack drove 90% of users to reset passwords within 24 hours—reducing the attack window by 80% (JPMC, 2023). Data from Google and Akamai shows standardized messaging can increase user response rates by up to 85%.
Tips for drafting effective communication templates:
- Draft clear, ready-to-use email and in-app notification templates for prompt communication with users after credential compromise.
- Templates should guide users on secure password reset steps, highlight next measures (such as enabling MFA), and reassure them about ongoing protection.
- Test templates with small user segments and refine for clarity and actionability.
- Update templates quarterly with input from legal, IT, and customer service to maintain consistent and effective messaging.
Summary Checklist for Securing Against Credential Stuffing
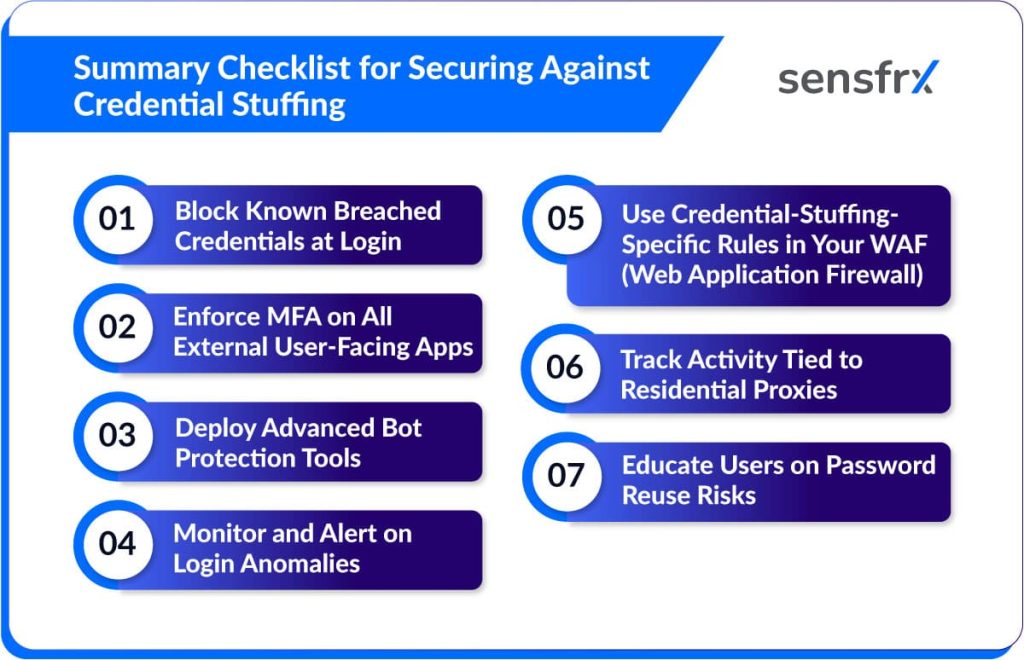
1. Block Known Breached Credentials at Login
Integrate your authentication system with a real-time breached credentials database (such as Have I Been Pawned or commercial APIs). Automatically check every login attempt and new password set against these databases—if a match is found, deny login or require the user to reset their password immediately.
How:
- Set up automated API calls to compare user credentials (hashed) against lists of known breaches.
- Alert users and enforce password resets if they try to use compromised passwords.
2. Enforce MFA on All External User-Facing Apps
Require multi-factor authentication (MFA) for every user accessing external-facing applications—such as accounts portals, webmail, or cloud platforms.
How:
- Implement MFA options like SMS codes, authenticator apps, or hardware tokens.
- Make MFA enrollment mandatory for all accounts and block access until enabled.
3. Deploy Advanced Bot Protection Tools
Implement bot management solutions or advanced Web Application Firewalls (WAF) that use AI to distinguish humans from credential-stuffing bots and act accordingly.
How:
- Deploy commercial bot mitigation platforms (Akamai, Cloudflare, Radware, etc.).
- Configure adaptive challenge mechanisms, rate limiting, and device fingerprinting to block suspicious bot traffic.
4. Monitor and Alert on Login Anomalies
Set up monitoring and automated alerts for unusual login behavior—such as impossible travel (logins from distant locations in a short period), rapid login attempts, or multiple failed logins.
How:
- Use SIEM, UEBA, or authentication logs to detect geographic or behavioral anomalies.
- Configure real-time alerts for security teams to investigate flagged incidents.
5. Use Credential-Stuffing-Specific Rules in Your WAF (Web Application Firewall)
Create WAF rules tailored for credential stuffing signs—such as blocking excessive login attempts, enforcing rate limits, and challenging requests that show bot-like behavior.
How:
- Apply predefined or custom WAF policies targeting known credential stuffing tactics.
- Review and tune WAF rules regularly for new attack patterns.
6. Track Activity Tied to Residential Proxies
Credential stuffing attackers channel their automated login attempts through proxy networks, especially residential ones, to make their traffic appear as legitimate user activity. Residential IPs are typically assigned to home internet users by ISPs, so requests from these addresses resemble genuine user logins and are less likely to be flagged by simple security filters. This helps attackers bypass geo-blocking and IP-based rate-limiting controls that would quickly block suspicious, repetitive activity from datacenter IPs or known malicious source
How:
- Leverage security solutions that can identify and flag proxy-originated logins.
- Automatically increase scrutiny or block traffic from suspicious proxy sources.
7. Educate Users on Password Reuse Risks
Run regular awareness campaigns explaining the dangers of password reuse and sharing best practices for creating unique passwords.
How:
- Send targeted emails, conduct training, and display reminders on login pages.
- Encourage the use of password managers for safe, unique password generation.
Conclusion
Credential stuffing isn’t just a security headache—it’s a direct threat to your revenue, reputation, and customer trust. As stolen credentials flood underground markets, the attacks are only getting faster and smarter. The best defense is to detect and stop them before they can cause damage. Sensfrx’s advanced fraud detection uses real-time monitoring, behavior analytics, and AI to block suspicious logins before they turn into costly breaches. Don’t wait for an incident—secure your business now with Sensfrx.
FAQs
Credential stuffing is an automated cyberattack in which hackers use lists of stolen usernames and passwords (often leaked in data breaches) to try logging into other websites and services, exploiting the widespread practice of password reuse.
Attackers acquire leaked credentials, often from previous breaches. Using bots or automated tools, they rapidly “stuff” these credential pairs into login forms across many platforms. Those that succeed provide immediate unauthorized access to user accounts, enabling fraud, data theft, or further compromise.
Credential stuffing can lead to data breaches, account takeover, direct financial losses, erosion of customer trust, reputational damage, regulatory fines, and operational disruption. Even a low success rate can produce thousands of compromised accounts when conducted at scale.
The attack succeeds because many users reuse passwords across multiple sites. Password reuse means that one breach at any service can put all a user’s other accounts at risk. Attackers leverage automation and distributed infrastructure to evade traditional security controls and maximize their reach.
Mitigation strategies include enforcing strong, unique passwords and promoting password manager usage, deploying multi-factor authentication (MFA), enabling bot detection and rate limiting on login endpoints, monitoring for abnormal login activity, and educating users about password hygiene.
