
Online fraud is getting smarter, and the old ways of stopping it are no longer enough.
Signals like IP addresses, device details, or passwords can be easily faked or manipulated by fraudsters.
Take this real-world scenario: a user logs into your platform from a familiar device. The IP checks out. The credentials are correct. No red flags. But within minutes, they update account settings, cash out stored value, and trigger a chargeback. By the time your system detects anything suspicious, the damage is already done.
This actually happened to a digital wallet provider. The attacker had stolen credentials and spoofed a trusted device fingerprint. Traditional security checks let them straight through. But behavioral analytics running in the background noticed something was off — erratic mouse movements and unfamiliar navigation patterns. It flagged the session as high risk, just in time to freeze the account and prevent further loss.
This highlights a crucial truth: static signals, while useful, have serious limitations. Fraudsters can spoof, recycle, or rotate them at scale. Relying solely on these signals is no longer enough for effective fraud detection.A more powerful approach is to analyze user behavior, how someone types, moves their mouse, or interacts with your app or site. These behavioral signals are far harder to fake, adding a deeper layer of protection and helping you detect fraud more accurately and in real time.
In this guide, we’ll explain how behavior-based fraud detection works, why it’s important, and how you can choose the right tool for your business.
What Is Behavioral Fraud Detection?
Behavioral analytics helps detect fraud by analyzing how users behave when they interact with your website or app. It looks at patterns in user activity, such as how they move the mouse, type on the keyboard, which pages they visit, what device they use, and even their IP address.
By studying this data, the system can spot unusual behavior that might signal fraud, such as account takeovers, fake signups, or suspicious payments. It then assigns a risk score based on how risky the behavior looks and can take action, like blocking access, triggering multi-factor authentication, or alerting a fraud team. As per a report, global losses from eCommerce fraud have increased by 16% over the past year.
For example, if a user has multiple failed login attempts or suddenly makes a large number of transactions, the system might flag it as a possible brute-force attack. It can also connect behavior across different channels (like mobile apps and websites) to get a clearer picture and build a more accurate risk model.
Behavioral Analytics vs Behavioral Biometrics
Behavioral analytics
Behavioral analytics tracks what users do during their session, their interactions with your website or app.
It answers questions like:
- What pages did they visit?
- How long did they stay on each page?
- What buttons did they click?
- Did they follow the usual purchase flow?
Example:
A customer usually visits your homepage, then checks two product pages, and adds one item to the cart. One day, the same user suddenly logs in and adds five items within 30 seconds without viewing any product details. That’s a behavioral anomaly — and behavioral analytics will catch it.
Behavioral biometrics
Behavioral biometrics tracks how users physically interact with their devices, based on their unique patterns.
It answers questions like:
- How fast and hard do they type?
- What’s their typing rhythm?
- How do they move their mouse or swipe their screen?
- How do they hold or tilt their phone?
Example:
Let’s say a fraudster steals someone’s login credentials and accesses their account. The device, IP, and password all check out. But behavioral biometrics detect that the person is typing much faster, with different pressure and rhythm than usual, and using the mouse in an unfamiliar pattern. That raises a red flag, even though everything else looks normal. Together, they create a profile of normal user behavior that helps flag anything suspicious.
Examples of Behavioral Signals Used in Fraud Detection

1. Typing Cadence
How fast and consistently someone types. For example, bots usually type instantly or too perfectly, while humans make small pauses or mistakes.
2.Mouse and Scroll Movements
Real users move their mouse naturally or scroll up and down at varying speeds. Bots tend to move in straight lines or make sudden clicks with no scrolling.
3. Touchscreen Gestures (for Mobile)
On phones, fraud systems can track how a user taps, swipes, or holds the device. A bot might tap the exact same spot every time , real humans don’t.
4. Session Duration and Navigation Patterns
If a user spends only a few seconds on checkout or jumps between steps in odd ways, it might be a sign of automated fraud. Genuine customers usually follow a more natural flow.
Why Behavioral Signals Are Hard to Spoof
It’s easy for fraudsters to fake an IP or use a stolen credit card — but it’s extremely hard to copy how a real person moves, types, or behaves online. These patterns are unique and nearly impossible to automate perfectly, making behavioral signals much harder to trick.
Key Benefits Over Traditional Detection (IP, Device, Geo)
- More accurate: Spots fraud even if other data looks fine
- Less intrusive: No need to block users with extra steps unless something looks off
- Fewer false positives: Real users are less likely to get flagged
- Stronger bot defense: Bots can’t mimic natural human behavior easily
Common Use Cases
Behavioral fraud detection is useful in many real-world situations. Here are some of the most common problems it helps solve:
Account Takeover (ATO)
Account Takeover happens when a fraudster breaks into a real customer’s account using stolen credentials. Behavioral signals can spot suspicious activity like logging in from a new device and quickly changing the password, then adding a new shipping address.
For example, if a customer usually logs in from Delhi but suddenly accesses their account from Russia and changes their delivery details within seconds, the system can flag this as an ATO attempt.
Synthetic Identity Fraud
Synthetic Identity Fraud involves creating fake identities using real and fake details mixed together — like a real phone number with a fake name and address. Behavioral detection can catch unusual patterns, like inconsistent typing speed or odd navigation behavior during signup.
For instance, someone signing up with perfect data but typing extremely fast and copying all details from a clipboard may be flagged as a bot creating a synthetic identity.
Bot Activity and Automated Abuse
Bots are automated scripts that can flood your site with fake logins, fake signups, or spam transactions. Behavioral tools detect when movements are too perfect, too fast, or too repetitive.
For example, if a bot creates 100 accounts in 10 minutes without moving the mouse or scrolling at all, the system quickly detects that the behavior doesn’t match how a real user behaves.
Promotion and Bonus Abuse in eCommerce/Gaming
Fraudsters create multiple fake accounts to claim welcome offers, discounts, or referral rewards repeatedly. Behavioral tools spot this by analyzing similar device patterns or how quickly users repeat actions across accounts.
For example, in a gaming app, if three new users from the same IP claim the sign-up bonus within seconds of each other using nearly identical navigation paths, it’s likely the same person gaming the system.
Insider Misuse in Corporate Settings
Sometimes, fraud isn’t external — it comes from employees misusing access. Behavioral monitoring can catch when someone suddenly starts downloading sensitive files or accessing systems outside work hours. For instance, if an employee who usually logs in during office hours suddenly starts accessing admin dashboards at 2 a.m. and exporting customer data, the system can alert the security team.
Behavioral Signal Collection Techniques

Understanding how users behave on your platform can be just as critical as knowing what transactions they make. Behavioral signal collection helps detect anomalies that traditional fraud rules may miss.
1. Passive vs Active Monitoring
Passive monitoring involves collecting user behavior data in the background, such as mouse movements, typing speed, or session duration, without interrupting the user’s experience.
Active monitoring, on the other hand, may involve direct prompts or user interaction, such as multi-step verification or behavioral tests triggered by suspicious actions.
Example: A legitimate user might naturally scroll and hesitate before purchasing; a bot might bypass this through scripted actions. Passive tracking would flag this unusual behavior without the user knowing.
2. Browser and Device-Based Signal Collection
This involves gathering details like browser fingerprinting, screen resolution, device orientation, installed plugins, and even battery status to create a unique identity profile for each user session.
Example: If a customer always logs in from an iPhone in India but suddenly signs in from a Linux desktop in Eastern Europe, the system can raise a red flag.
3.Combining Behavioral Data with Traditional Fraud Signals
Behavioral patterns become more powerful when combined with rule-based fraud indicators (e.g., velocity checks, IP reputation). This hybrid approach strengthens detection capabilities.
Example: A transaction might pass basic rules but still get flagged because the user’s typing pattern drastically changed compared to their previous logins.
4. Federated Learning and Privacy-Preserving Techniques
Modern systems use federated learning to train fraud detection models on different devices without sharing personal data. When combined with privacy tools like differential privacy, this approach helps detect fraud while keeping user information safe.
Example: A fraud model learns from login behavior across 100 retail apps without aggregating the actual data in a single location, preserving customer privacy.
Modeling & Detection Approaches
Understanding how fraud detection works behind the scenes can help you choose the right tool Here are the key methods used in behavioral fraud detection:
1. Rule-Based Pattern Detection
This approach uses if-then rules to catch known fraud patterns. It’s like setting up red flags based on specific behaviors. For instance, if someone places multiple orders within minutes, all going to the same address but using different emails, the system sees this as suspicious and blocks it automatically. Rule-based systems are quick and easy to set up, but they may miss new or evolving fraud tricks.
2. Machine Learning Models (Anomaly Detection, User Clustering)
Unlike fixed rules, machine learning models learn what normal behavior looks like across many users and then flag anything that stands out. For example, if most users in your store spend a few minutes browsing and add 1–2 items to the cart, but someone goes straight to checkout with 10 expensive items in 30 seconds, the system notices this as unusual behavior and raises a red flag. These models are great for spotting new and unexpected types of fraud.
3. Risk Scoring Frameworks
Here, every user action is given a score based on how risky it looks. The system adds up these scores during the session to decide whether to allow, flag, or block the activity. A login from a new country, followed by a fast checkout with saved payment info and a different shipping address, might push the total risk score over the safe limit, leading to a verification step or order block.
Below is a small snapshot from the Sensfrx dashboard that shows the risk score:
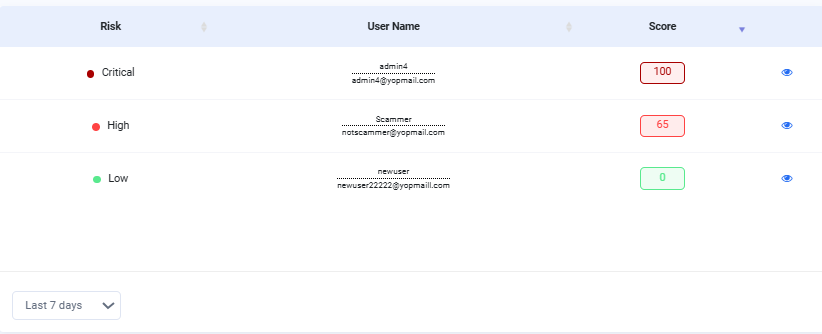
4. Continuous Authentication vs Point-in-Time Detection
Some tools only check for fraud at key moments, like login or payment (point-in-time detection), while others keep watching the user’s behavior throughout the entire session (continuous authentication). Imagine someone logs in normally but then quickly changes the email, resets the password, and adds a new address — all in less than a minute. Continuous systems can catch this mid-session, even if the login itself looks clean.
5. Feedback Loops: Analyst Review + Auto-Labeling
Fraud systems get better over time by learning from what you or your team mark as real fraud. Say you manually review a flagged order and confirm it was fake — the system remembers this and uses that pattern to catch similar fraud in the future without needing manual checks. This feedback loop helps reduce false positives and improves detection accuracy over time.
Challenges in Behavioral Fraud Detection
While behavioral signals are powerful for spotting fraud, using them effectively comes with some challenges:

1. False Positives and User Experience Trade-offs
Sometimes, fraud systems can mistakenly flag a real customer as suspicious (a false positive). If this happens too often, like asking real users for extra verification, it can frustrate them and hurt the customer experience.
Example: A regular customer logs in from a different device during travel, and the system wrongly treats them like a threat.
2. Variability Across Devices, Browsers, and Locations
User behavior can look very different depending on the device or browser they use, or where they’re located. This makes it hard to create consistent behavioral models.
Example: Someone might scroll slowly on a mobile phone but quickly on a laptop — both are normal, but they look very different to a fraud detection system.
3. Privacy, Consent, and Regulatory Considerations
Collecting behavioral data — like how someone types or moves their mouse — may raise privacy concerns. You need clear user consent and must follow laws like GDPR or CCPA when tracking behavior.
Example: Websites may need to show consent pop-ups and let users opt out of tracking.
4. Model Drift and Retraining Needs
Over time, user behavior changes. If your fraud detection model doesn’t adapt, it becomes less accurate — this is called model drift. Systems need regular updates to stay effective.
Example: After a new app update, people interact with your site differently — if the model isn’t retrained, it might start flagging normal behavior as suspicious.
5. Data Retention and Storage Architecture
Collecting behavioral data creates a large volume of information. You need a well-organized system to store, manage, and protect this data, without keeping it longer than necessary.
Example: Think of it like storing security footage. You don’t need to keep every second forever, but you must store enough, keep it secure, and delete it when it’s no longer needed — all while following data protection rules.
Evaluating Behavioral Fraud Detection Tools
Here’s a checklist of the key features you should look for:
1. Real-time decision-making
The tool should detect and respond to suspicious behavior as it happens, not after the damage is done, such as blocking a fraudulent checkout attempt instantly, rather than flagging it later.
2. Session-Level Insights
A session refers to the entire period of activity by a user from the moment they enter your website or app until they leave, log out, or become inactive for a set time. You should be able to see what a user did during an entire session, like how they moved, clicked, or hesitated.
Example: A bot might complete a sign-up form in 2 seconds. A real user might take 30 seconds, tab between fields, or pause.
3. Explainability and Audit Logs
The system should show why it flagged something, not just say “this is fraud.” Audit logs help teams review and justify decisions.
Below is an example from the Sensfrx dashboard listing the reasons why a particular transaction was flagged.
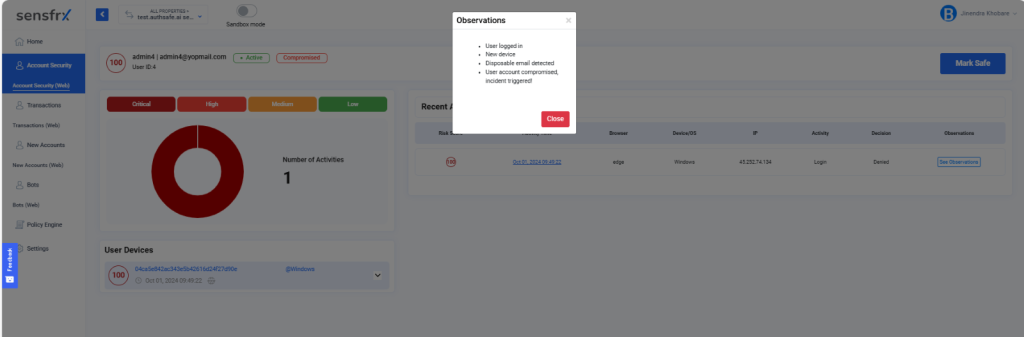
4. SDK vs JavaScript vs Backend Integration
Different tools offer different ways to connect:
- JavaScript: Easy to drop into a website.
- SDK: Ideal for mobile apps.
- Backend API: Useful if you want more control or to integrate with other systems.
Each has trade-offs in ease of use, data depth, and performance.
Deployment Options and Integration Methods
Check if the tool can be deployed in the cloud, on-premises, or in a hybrid environment, and how smoothly it connects with your existing tech stack.
Example: Can it plug into your CRM, payment gateway, or internal risk engine?
Support for Hybrid Models (Human + AI)
The best tools allow automation and manual oversight. They use AI to catch patterns fast, but also let human analysts review or override decisions.
Example: A flagged transaction might be auto-blocked, but still shown to a fraud analyst for final judgment.
Case Management and Analyst Tooling
Analysts should be able to group related fraud cases, add notes, and track outcomes in one place. So, look for dashboards that offer investigation views and case-tracking features. These help your fraud team work faster and more effectively.
Future Trends
Fraud detection is getting smarter by combining new technologies with behavioral data and three out of four eCommerce businesses are planning to invest more in fraud prevention in the near future. Here are some development trends to look forward to:
1. Combining Behavior fraud detection with AI That Understands Intent
New systems combine behavioral biometrics (such as typing, swiping, and clicking) with AI models that aim to understand the user’s intended actions.
This helps tell the difference between a real customer and a fraudster, even if they’re using the same device.
Example: A person checking their balance and a fraudster trying to transfer money quickly may behave differently; the system can now “sense” their intent.
2. Linking Sessions to Spot Fraud Rings
Instead of just looking at one visit, systems now connect multiple sessions across different accounts or devices to detect fraud networks.
Example: If five different accounts use the same typing style, device info, and behavior, they might all be controlled by the same fraudster.
3. Smarter Logins Based on Behavior
Authentication (like logging in) is becoming adaptive — it changes based on how risky the user’s behavior looks.
Example: If a user logs in from their usual device and types like they always do, they get in easily. If something seems off, the system may ask for extra steps like an OTP.
4. Privacy-Friendly Ways to Use Behavior Data
Companies are now using privacy-enhancing technologies to protect personal data while still using behavior to detect fraud.
Example: It’s like using a blurry photo to see the shape of a person without knowing who they are — you still get useful info without invading privacy.
How Sensfrx Helps in Behavioral Analytics in Fraud Detection
Sensfrx is equipped with sophisticated tools and strategies to combat various forms of fraud:
- Strong Encryption: By employing end-to-end encryption, Sensfrx shields sensitive user data, ensuring it remains secure and inaccessible to unauthorized parties. This proactive measure prevents potential data breaches and safeguards against identity theft.
- Device Fingerprinting: Sensfrx captures detailed information about devices accessing the platform, including browser types, operating systems, and IP addresses. It actively monitors these devices for any abnormal behaviors that may signal fraudulent activities. By flagging suspicious devices in real-time, Sensfrx mitigates risks before they escalate into security breaches.
- Smart Algorithm: The platform continuously tracks and analyzes user behaviors, login patterns, and transaction activities. This intelligent monitoring system promptly identifies deviations from normal usage patterns, enabling swift detection of suspicious activities that could indicate fraud.
- Dynamic Risk Scoring: Sensfrx evaluates transactions in real-time using a dynamic risk scoring mechanism. This approach factors in variables such as user behavior history, device information, and transaction patterns to assess the likelihood of fraud. By assigning risk scores instantly, Sensfrx empowers businesses to respond promptly to potential threats, minimizing financial losses and protecting user trust.
- Fraud Validators: Leveraging advanced fraud detection capabilities, Sensfrx swiftly identifies and verifies instances of fraudulent activities. This proactive detection allows for immediate action to prevent fraud before it impacts users or compromises business operations.
- Smart Fraud Detection: Through the application of machine learning algorithms, Sensfrx detects sophisticated fraud patterns such as account takeovers and fraudulent transactions. By continuously learning from data insights, Sensfrx evolves its detection capabilities to stay ahead of emerging fraud tactics, ensuring robust protection against evolving threats.
Conclusion
Legacy fraud detection tools suffer from limitations, such as too many false positive alerts, and whenever they detect fraudulent activity, it’s too little, too late. To keep pace with the evolving complexity of attackers, they need to continuously upgrade their behavioral data models to process emerging threats. Sensfrx employs sophisticated behavioral analytics-based fraud models to examine activities throughout the customer lifecycle. Get in touch with us to know more about how it can help.
Behavioral fraud detection involves analyzing how users interact with a website or app — such as their typing speed, mouse movements, click patterns, or session behavior — to detect suspicious or abnormal activity.
Why it matters:
Traditional signals like IP address or device ID can be spoofed. But behavior is harder to fake. It helps businesses detect sophisticated fraud attempts (like account takeovers or bot attacks) even when static credentials or devices seem legitimate.
Behavioral biometrics looks at how users physically interact with a device, typing rhythm, swipe gestures, mouse movement, and more, based on human motor behavior.
Device fingerprinting, on the other hand, collects static technical details about the device itself like browser type, OS version, screen size, and plugins.
Key difference:
• Device fingerprinting checks what device is being used.
• Behavioral biometrics checks who is using the device, based on how they use it.
Not yet — but it can strengthen them.
Behavioral analysis is typically used as a passive, continuous layer of security. It doesn’t replace passwords or MFA but can complement them by silently monitoring behavior after login.
In some advanced systems, it may even be used for frictionless authentication, where a user doesn’t need to re-authenticate unless their behavior seems suspicious.
• Privacy concerns: Users may be uncomfortable with continuous behavior tracking, even if it’s anonymous.
• False positives: Unusual behavior (e.g., using a new device or being in a hurry) might trigger alerts for genuine users.
• Integration complexity: Behavioral systems often need machine learning and data pipelines, which can be costly or time-consuming to implement.
• Data volume: Collecting and analyzing behavior in real time requires scalable infrastructure.
Behavioral fraud detection is especially valuable for industries that handle sensitive data or financial transactions:
• Banking and Fintech: To prevent account takeovers, fraudulent transfers, and identity theft.
• E-commerce: To stop bots, fake accounts, coupon abuse, and payment fraud.
• Healthcare: For securing patient portals and detecting unauthorized access.
• Insurance: To catch fraud in claims processing or user identity spoofing.
• Gaming and Gambling: To detect multi-accounting, bot activity, and collusion.




